HTB-Soulmate
本文最后更新于 2025年9月14日 晚上
难度:easy,没啥意思。文件上传拿 shell,再利用 Erlang 加载的 OS 模块命令执行
信息收集
nmap
1 | |
ffuf
1 | |
CVE-2025-31161+文件上传
有一个 ftp 子域名
1 | |
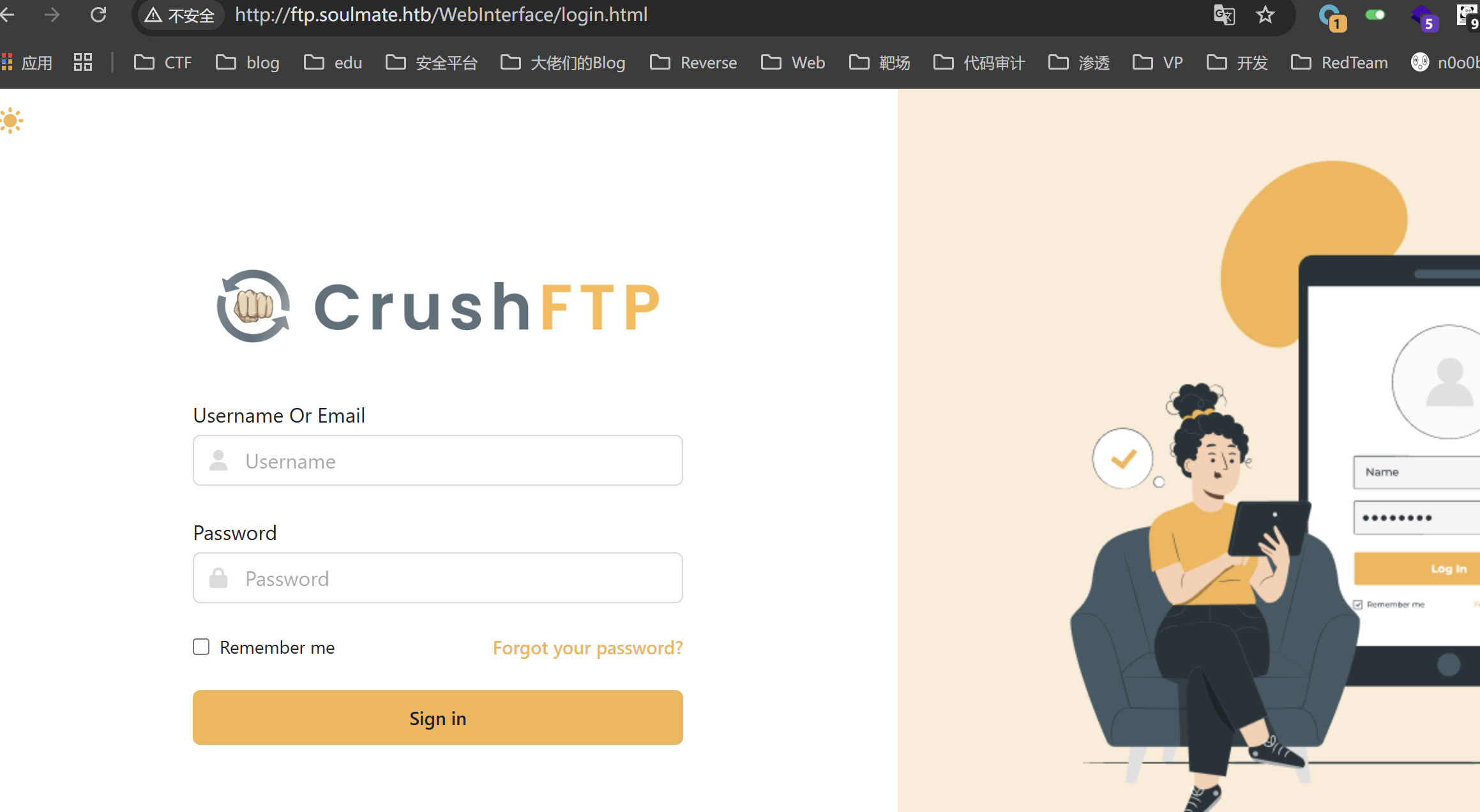
CrushFTP,看网页源代码可以发现版本 11.W.657,找到几个身份验证的 CVE
CVE-2025-31161 可以用
1 | |
执行 poc
1 | |
在 User Manage 模块发现有几个用户
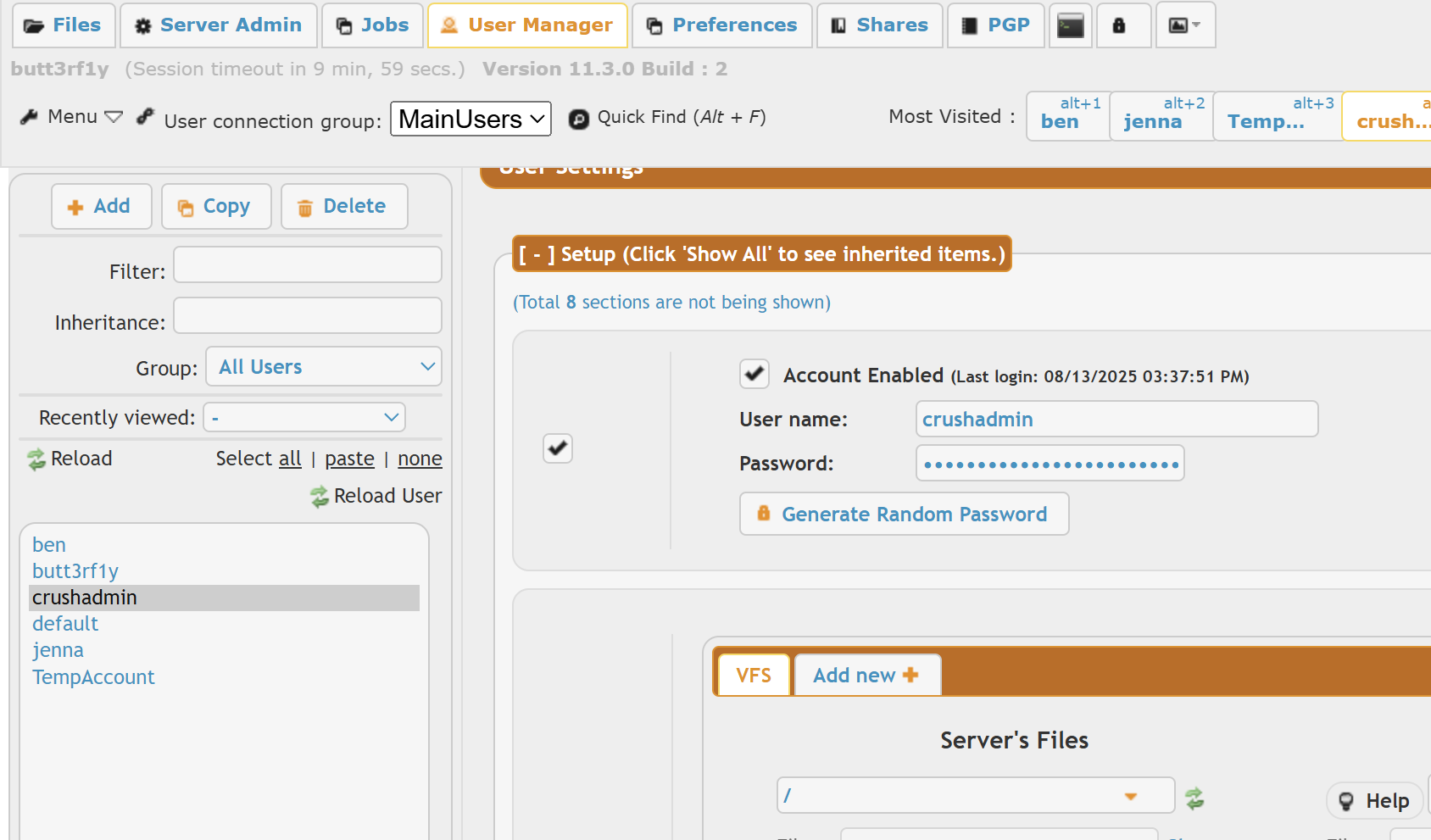
可以修改用户密码,先改 ben 的,登录进去发现能进行文件上传,上马,马在一段时间后会被删除,所以权限维持动作需要快点
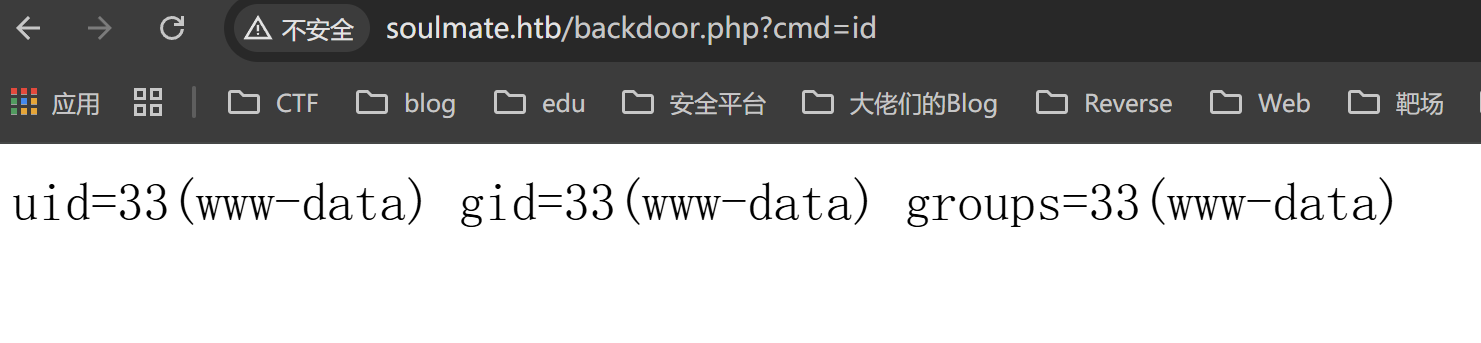
反弹 shell,在 /usr/local/lib/erlang_login 的目录下找到 start.escript
1 | |
拿到用户密码,ssh 登录
1 | |
拿到 userflag
利用 Erlang 服务加载的 os 模块命令执行
查看端口开放情况,发现 2222 端口运行了基于 Erlang 的 SSH 服务
1 | |
登录查看
1 | |
运行 m(). 查看加载的模块
加载了 os 模块,OS command and code execution in Erlang and Elixir applications,os 模块运行命令
1 | |
已经是 root 了,拿 flag 顺手的事
HTB-Soulmate
http://example.com/2025/09/14/HTB-Soulmate/