1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
| import sys
src_data = [
0x1f, 0x52, 0xdc, 0x4d, 0x2c, 0x84, 0x80, 0x91, 0xd6, 0x18, 0x5b, 0x4e, 0xba, 0xc3, 0x0d, 0x71,
0x56, 0x52, 0xdc, 0x4d, 0x2c, 0x84, 0x80, 0xd8, 0xd6, 0x18, 0x72, 0x4e, 0xba, 0x61, 0x0d, 0x71,
0x34, 0x52, 0xdc, 0x4d, 0x2c, 0x84, 0x80, 0x5c, 0xd6, 0x18, 0x43, 0x4e, 0xba, 0x65, 0x0d, 0x71,
0xc9, 0x52, 0xdc, 0x4d, 0x2c, 0x84, 0x80, 0x28, 0xd6, 0x18, 0x61, 0x4e, 0xba, 0x50, 0x0d, 0x71,
0xd4, 0x0b, 0xdc, 0x4d, 0x9b, 0x84, 0x80, 0x77, 0xd6, 0x18, 0x7d, 0x34, 0xba, 0xca, 0x47, 0x71,
0xd4, 0x41, 0xdc, 0x4d, 0x94, 0x84, 0x80, 0x77, 0xd6, 0x18, 0x7d, 0xda, 0xba, 0xca, 0x62, 0x71,
0xd4, 0x36, 0xdc, 0x4d, 0x06, 0x84, 0x80, 0x77, 0xd6, 0x18, 0x7d, 0xe1, 0xba, 0xca, 0xac, 0x71,
0xd4, 0xc2, 0xdc, 0x4d, 0xe7, 0x84, 0x80, 0x77, 0xd6, 0x18, 0x7d, 0xea, 0xba, 0xca, 0x60, 0x71,
0xd4, 0x52, 0x6f, 0x4d, 0x2c, 0x37, 0x80, 0x77, 0x00, 0x18, 0x7d, 0x4e, 0xba, 0xca, 0x0d, 0x80,
0xd4, 0x52, 0x09, 0x4d, 0x2c, 0x3a, 0x80, 0x77, 0x40, 0x18, 0x7d, 0x4e, 0xba, 0xca, 0x0d, 0x7b,
0xd4, 0x52, 0x62, 0x4d, 0x2c, 0x93, 0x80, 0x77, 0x54, 0x18, 0x7d, 0x4e, 0xba, 0xca, 0x0d, 0x36,
0xd4, 0x52, 0xf0, 0x4d, 0x2c, 0x54, 0x80, 0x77, 0x10, 0x18, 0x7d, 0x4e, 0xba, 0xca, 0x0d, 0x17,
0xd4, 0x52, 0xdc, 0x1f, 0x2c, 0x84, 0xc8, 0x77, 0xd6, 0x4b, 0x7d, 0x4e, 0x17, 0xca, 0x0d, 0x71,
0xd4, 0x52, 0xdc, 0x75, 0x2c, 0x84, 0x76, 0x77, 0xd6, 0x25, 0x7d, 0x4e, 0xcf, 0xca, 0x0d, 0x71,
0xd4, 0x52, 0xdc, 0x2b, 0x2c, 0x84, 0x22, 0x77, 0xd6, 0x08, 0x7d, 0x4e, 0x16, 0xca, 0x0d, 0x71,
0xd4, 0x52, 0xdc, 0x3e, 0x2c, 0x84, 0x33, 0x77, 0xd6, 0x81, 0x7d, 0x4e, 0x2d, 0xca, 0x0d, 0x71,
]
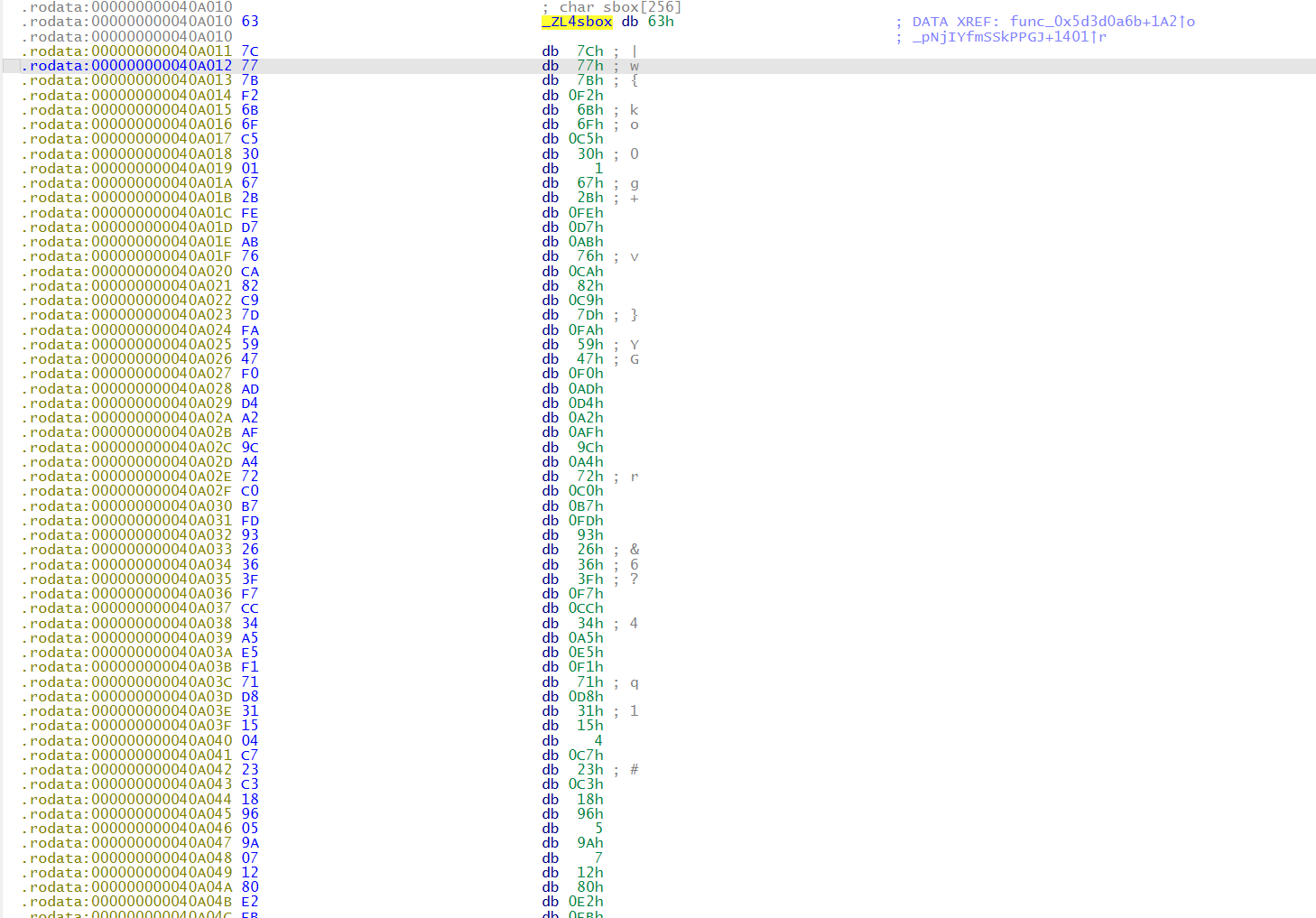
sbox_data = [
0x7c, 0x77, 0x7b, 0xf2, 0x6b, 0x6f, 0xc5, 0x30, 0x01, 0x67, 0x2b, 0xfe, 0xd7, 0xab, 0x76,
0xca, 0x82, 0xc9, 0x7d, 0xfa, 0x59, 0x47, 0xf0, 0xad, 0xd4, 0xa2, 0xaf, 0x9c, 0xa4, 0x72,
0xc0, 0xb7, 0xfd, 0x93, 0x26, 0x36, 0x3f, 0xf7, 0xcc, 0x34, 0xa5, 0xe5, 0xf1, 0x71, 0xd8,
0x31, 0x15, 0x04, 0xc7, 0x23, 0xc3, 0x18, 0x96, 0x05, 0x9a, 0x07, 0x12, 0x80, 0xe2, 0xeb,
0x27, 0xb2, 0x75, 0x09, 0x83, 0x2c, 0x1a, 0x1b, 0x6e, 0x5a, 0xa0, 0x52, 0x3b, 0xd6, 0xb3,
0x29, 0xe3, 0x2f, 0x84, 0x53, 0xd1, 0x00, 0xed, 0x20, 0xfc, 0xb1, 0x5b, 0x6a, 0xcb, 0xbe,
0x39, 0x4a, 0x4c, 0x58, 0xcf, 0xd0, 0xef, 0xaa, 0xfb, 0x43, 0x4d, 0x33, 0x85, 0x45, 0xf9,
0x02, 0x7f, 0x50, 0x3c, 0x9f, 0xa8, 0x51, 0xa3, 0x40, 0x8f, 0x92, 0x9d, 0x38, 0xf5, 0xbc,
0xb6, 0xda, 0x21, 0x10, 0xff, 0xf3, 0xd2, 0xcd, 0x0c, 0x13, 0xec, 0x5f, 0x97, 0x44, 0x17,
0xc4, 0xa7, 0x7e, 0x3d, 0x64, 0x5d, 0x19, 0x73, 0x60, 0x81, 0x4f, 0xdc, 0x22, 0x2a, 0x90,
0x88, 0x46, 0xee, 0xb8, 0x14, 0xde, 0x5e, 0x0b, 0xdb, 0xe0, 0x32, 0x3a, 0x0a, 0x49, 0x06,
0x24, 0x5c, 0xc2, 0xd3, 0xac, 0x62, 0x91, 0x95, 0xe4, 0x79, 0xe7, 0xc8, 0x37, 0x6d, 0x8d,
0xd5, 0x4e, 0xa9, 0x6c, 0x56, 0xf4, 0xea, 0x65, 0x7a, 0xae, 0x08, 0xba, 0x78, 0x25, 0x2e,
0x1c, 0xa6, 0xb4, 0xc6, 0xe8, 0xdd, 0x74, 0x1f, 0x4b, 0xbd, 0x8b, 0x8a, 0x70, 0x3e, 0xb5,
0x66, 0x48, 0x03, 0xf6, 0x0e, 0x61, 0x35, 0x57, 0xb9, 0x86, 0xc1, 0x1d, 0x9e, 0xe1, 0xf8,
0x98, 0x11, 0x69, 0xd9, 0x8e, 0x94, 0x9b, 0x1e, 0x87, 0xe9, 0xce, 0x55, 0x28, 0xdf, 0x8c,
0xa1, 0x89, 0x0d, 0xbf, 0xe6, 0x42, 0x68, 0x41, 0x99, 0x2d, 0x0f, 0xb0, 0x54, 0xbb, 0x16,
]
full_sbox = [0x63] + sbox_data
init_vec = bytes([
0x45, 0xBA, 0x23, 0x7D, 0xEB, 0xC4, 0xC2, 0x0F,
0xDA, 0x39, 0x62, 0x61, 0x93, 0xF6, 0x64, 0xB4,
])
rcon_list = [0x00, 0x01, 0x02, 0x04, 0x08, 0x10, 0x20, 0x40, 0x80, 0x1B, 0x36]
def generate_shift_map():
original_indices = list(range(16))
rows = [[], [], [], []]
for c in range(4):
for r in range(4):
rows[r].append(original_indices[c * 4 + r])
rows[1] = rows[1][1:] + rows[1][:1]
rows[2] = rows[2][2:] + rows[2][:2]
rows[3] = rows[3][3:] + rows[3][:3]
mapped_indices = []
for c in range(4):
for r in range(4):
mapped_indices.append(rows[r][c])
return mapped_indices
index_map = generate_shift_map()
inv_sbox_table = [0] * 256
for i, v in enumerate(full_sbox):
inv_sbox_table[v] = i
def gmul(a, b):
p = 0
for _ in range(8):
if b & 1: p ^= a
hi = a & 0x80
a = (a << 1) & 0xFF
if hi: a ^= 0x1B
b >>= 1
return p & 0xFF
def mix_cols(state):
out = [0] * 16
for c in range(4):
p = state[4*c : 4*c+4]
out[4*c+0] = gmul(0x02, p[0]) ^ gmul(0x03, p[1]) ^ p[2] ^ p[3]
out[4*c+1] = p[0] ^ gmul(0x02, p[1]) ^ gmul(0x03, p[2]) ^ p[3]
out[4*c+2] = p[0] ^ p[1] ^ gmul(0x02, p[2]) ^ gmul(0x03, p[3])
out[4*c+3] = gmul(0x03, p[0]) ^ p[1] ^ p[2] ^ gmul(0x02, p[3])
return out
def reverse_keysched(target_key):
w = [None] * 44
for i in range(4):
w[40+i] = target_key[4*i : 4*i+4]
for i in range(43, 3, -1):
if i % 4 != 0:
w[i-4] = bytes(a ^ b for a, b in zip(w[i], w[i-1]))
else:
rot = w[i-1][1:] + w[i-1][:1]
sub = bytes(full_sbox[x] for x in rot)
r_val = rcon_list[i // 4]
xor_res = bytes([sub[0] ^ r_val, sub[1], sub[2], sub[3]])
w[i-4] = bytes(a ^ b for a, b in zip(w[i], xor_res))
return b"".join(w[0:4])
blocks = [src_data[i*16 : (i+1)*16] for i in range(16)]
precalc_mix = []
base_arr = list(init_vec)
for i in range(16):
tmp = base_arr[:]
tmp[i] = 0
precalc_mix.append(mix_cols(tmp))
final_key_array = [0] * 16
for p in range(16):
mix_idx = index_map[p]
cands = []
for k_byte in range(256):
prev_key_byte = None
consistent = True
for i in range(16):
out_val = blocks[i][p]
mix_val = precalc_mix[i][mix_idx]
val = inv_sbox_table[out_val ^ k_byte] ^ mix_val
if prev_key_byte is None:
prev_key_byte = val
elif prev_key_byte != val:
consistent = False
break
if consistent:
cands.append(k_byte)
if len(cands) == 1:
final_key_array[p] = cands[0]
else:
print(f"Error at byte {p}: found {len(cands)} candidates")
sys.exit(1)
final_key_bytes = bytes(final_key_array)
master_key = reverse_keysched(final_key_bytes)
print(f"Key: {master_key.hex()}")
|