DASCTF 2025下半年赛-Reverse
本文最后更新于 2025年12月7日 下午
ezmac
加密逻辑,简单异或
1 | |
解密脚本
1 | |
flag
1 | |
androidfile
Java 层生成两个随机字符串 s、s1 作为 AES 的 key 和 iv,再进行 RSA 公钥加密,调用 native 层
1 | |
给了数据
1 | |
so 里面是标准 RC4 加密

1 | |
解得 RSA 加密后的 key 和 iv,最后用私钥进行解密密文
1 | |
拿到 flag
1 | |
login
client 端发送了三个字段,account,key,password
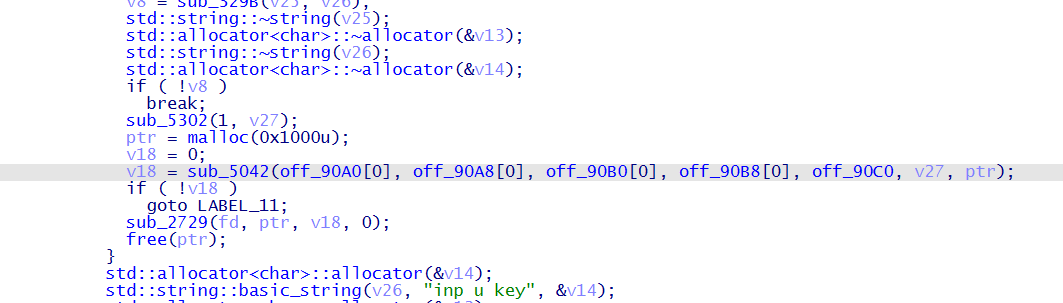
并且 sub_49DD 和 sub_4125 函数这里进行了 AES-128 CBC 加密
1 | |
server 这边收到的数据依次进行校验,account -> byte_C1A0,key -> byte_C0A0,password -> byte_CA20
account 和 key 验证之后调用 sub_73B2 函数进行了 RSA 解密,这里拿到 RSA 私钥也就是 off_C2F0 ,然后对这两个字段的数据进行解密
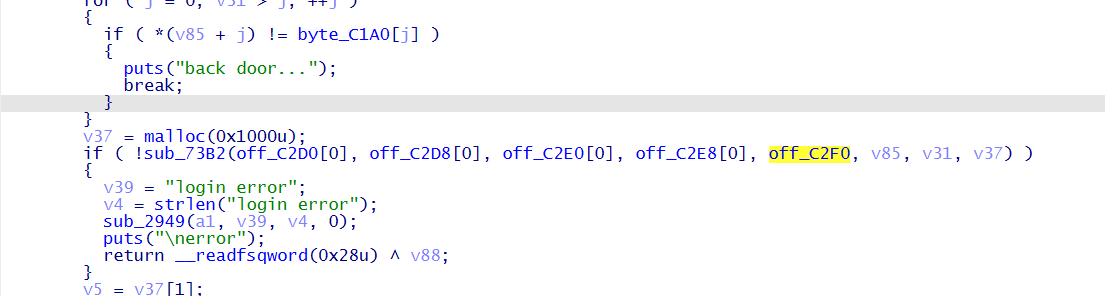
1 | |
解得 key 和 iv
1 | |
根据拿到的 key 和 iv 解密
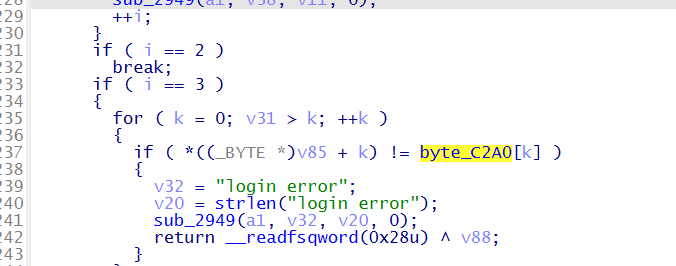
1 | |
得到 flag
1 | |
androidfff
flutter 框架的 apk,blutter 解包后 IDA 加载 libapp.so 导入符号表(结束之后 p3c0wn 师傅给我说这个可以直接看 asm\untitled3\main.dart 文件,确实这样不需要载入符号表了更方便^~^)
跟进定位到 untitled3_main__FlagCheckerState::ctor_2f7c1c 这里,初始化一个 FlagCheckerState 对象,并向对象内部写入一段字节数组进行校验,这就是密文
1 | |
这里在进行 xor
1 | |
因为 xor 函数中进行了 result = (2 * (v3 ^ 0x32)) 操作,所以对密文除以 2 才是真正的密文
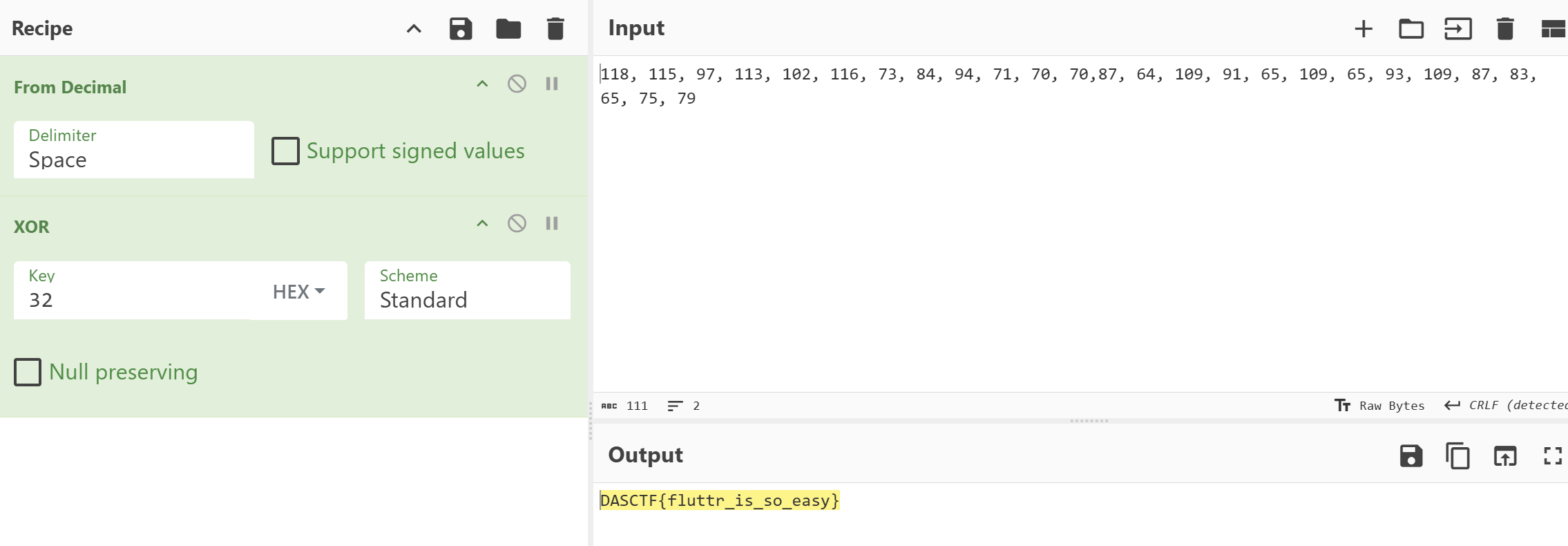
1 | |