2025极客大挑战-Reverse
本文最后更新于 2025年12月4日 晚上
前面的题比较简单就没写 wp,后面的一些题挺有意思的,遂记录

Mission Ghost Signal
本质是 AES-128-CBC 加密,但 S-box、MixColumns 都是自定义的
进入 main 函数分析,输入长度必须 25 字符,IV 固定 1145141145144332”,Key 在 aSyclover2025ge 中就是 Syclover2025Geek,大概是 AES 加密,最后结果与 byte_406020 比较
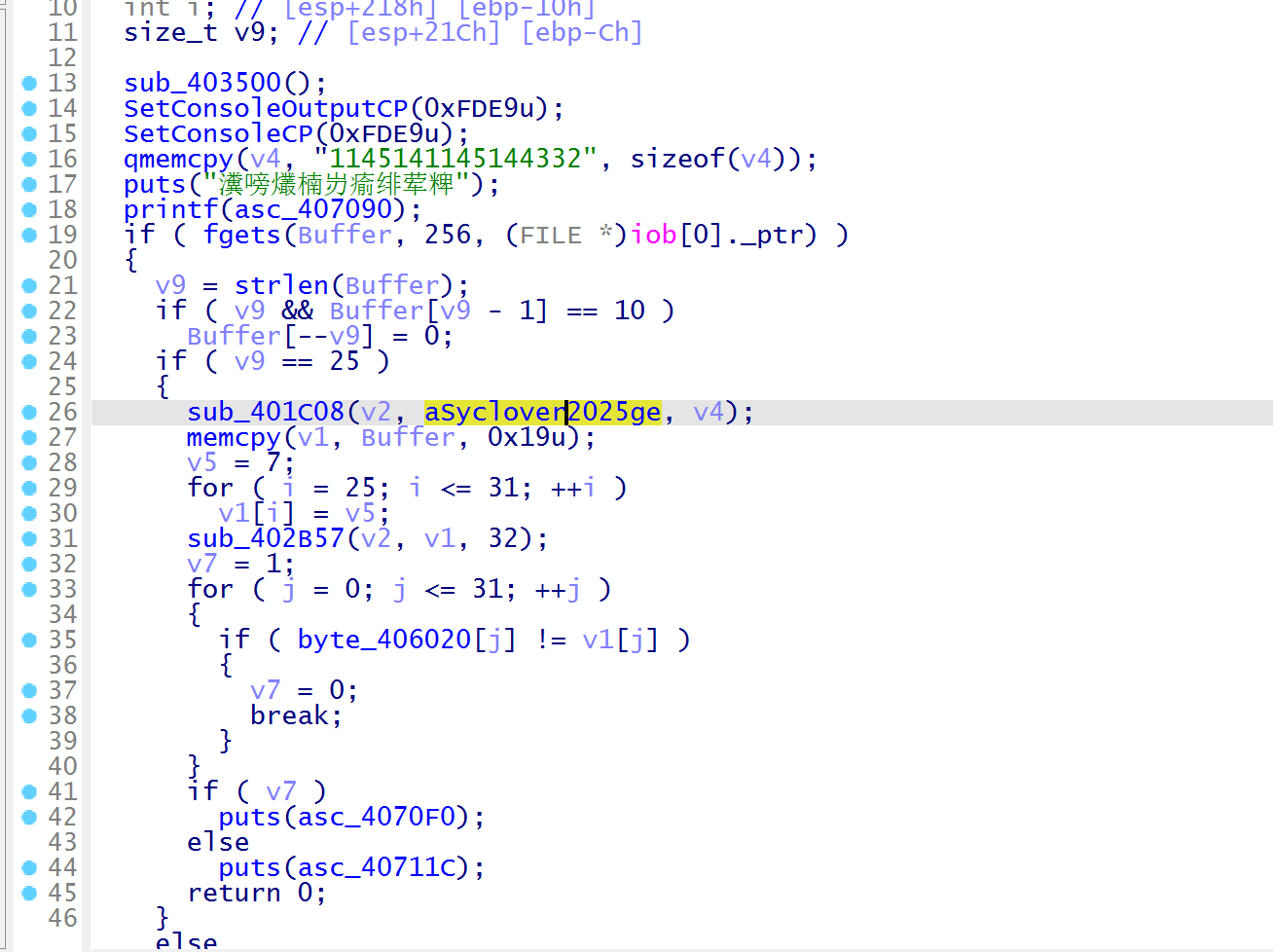
byte_406020
1 | |
sub_402B57:先进入 sub_402B11 异或再进入 sub_402992 加密
1 | |
继续跟进 sub_401D41 -> sub_401929 -> sub_4018B6 -> sub_4017B8
1 | |
sub_4015B4 自定义的 SBOX 变换
1 | |
跟进 sub_401C08 -> sub_4019B7,这里是在进行密钥扩展
1 | |
unk_407064 这组数据就是 RCON
1 | |
解密脚本如下:
1 | |
解除来的是:
1 | |
作为压缩包密码,打开有一个 wav 音频,可以听出这个音频像信号,所以有可能是 sstv
1 | |
解出来是一个有二维码的图片,识别不出来,然后我拿手机微信识别出来的,会跳转网页下载一个 secret.zip 文件

解压得到一个音频文件,摩斯电码,在线网站解码
1 | |
hex + base64 解密
1 | |
stack_bomb
一个 tea 加密
无法反编译,分析汇编代码
1 | |
输入的 32 字节:
1 | |
sub_411FE0 中找到 key:1,2,3,4
1 | |
跟踪到 sub_411920,这里是加密核心,循环 a48 的值次数
1 | |
这里对应 key
1 | |
x 和 y,sum
1 | |
这里一堆 STACK[],是因为反编译失败,要获取每个 STACK 代表什么可以在前面 push 每个调用的函数 return 下断点,调试时会调用此函数,同时可以获取 delta 和 key 值
1 | |
由此可还原 AES 加密逻辑
1 | |
解密脚本如下
1 | |
拿到 flag
1 | |
GeekBinder
加密很简单,按 i%8 和 geek2025 异或,密文在 attr_get_hidden_cipher 函数中
1 | |
解密脚本
1 | |
1 | |
Her
这个题有个 SEH,也就是 Windows 的异常处理,反编译隐藏正确的调用代码
主要跟进 sub_4011B3() 函数
1 | |
一直跟进到 sub_401D30 函数,这里有一个 BUG 函数,反汇编能看到 SEH 的关键代码
1 | |
如下,这里是 SEH 链的注册,这里注册了三个函数,根据栈的规则 sub_401091 最先被调用,sub_401091->sub_401186->sub_401181
1 | |
跟进 sub_401091 ,与 0xAA 异或
1 | |
并且这里还调用了 sub_401186 函数
1 | |
跟进 sub_401186 ,进行加法
1 | |
并且也调用了 sub_401181
1 | |
sub_401181 这边进行了循环移动
1 | |
加密比较简单,动调获取密文,主要是 SEH 处理,解密脚本如下
1 | |
拿到 flag
1 | |
ez_Android
加密的 flag 密文在 res/raw 中,function1 为 des 加密,key 为 12345678
1 | |
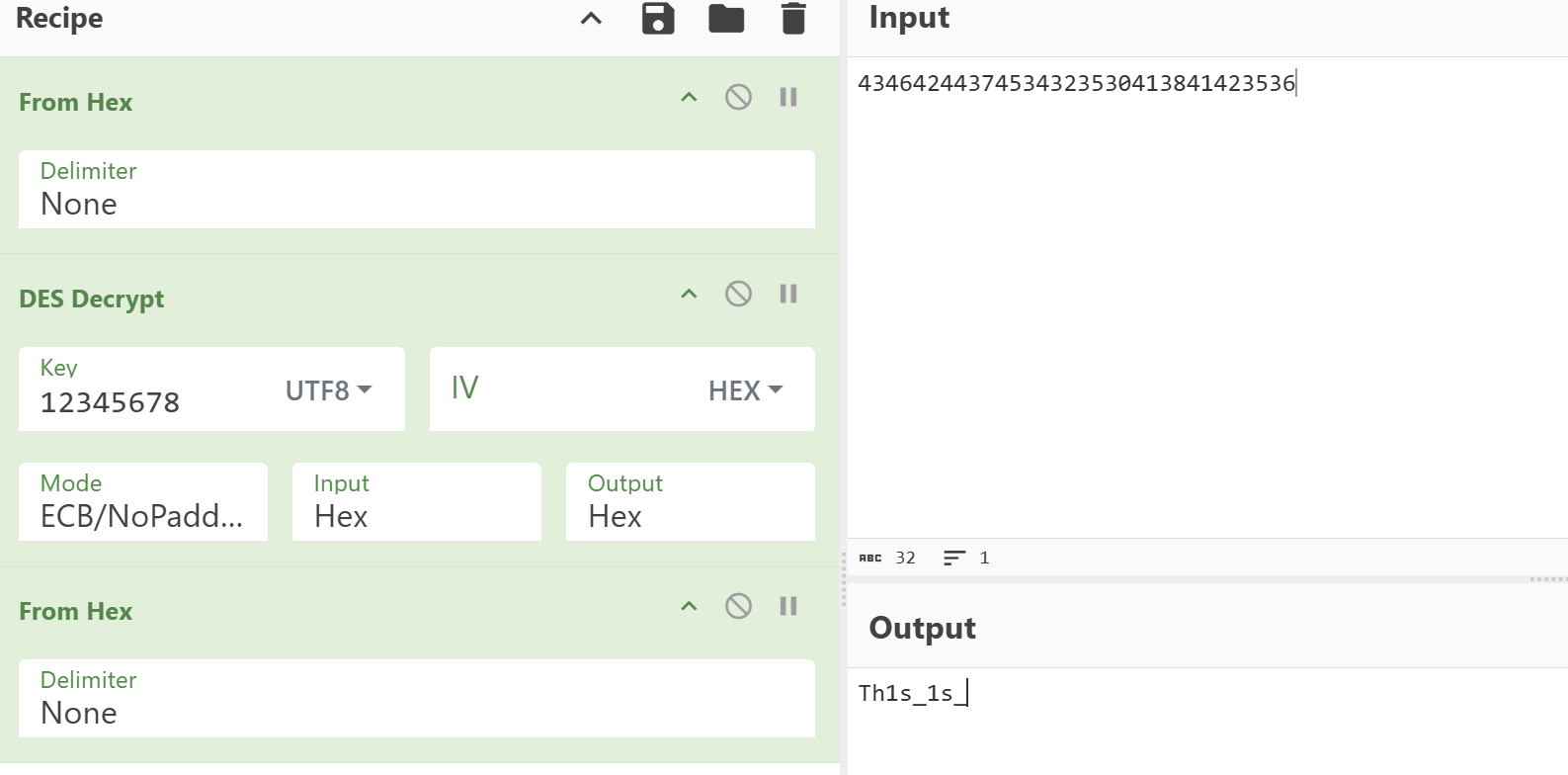
1 | |
function2,JNI_onLoad 动态调用了真正的 so,获取真正加载的 so
1 | |
load_real_so 加载真实 so 的 wrapper,它从内存中解密内置的 encrypted_so →->写入临时文件 -> dlopen -> dlsym 加载真正的 JNI 方法
1 | |
解密 so 脚本如下
1 | |
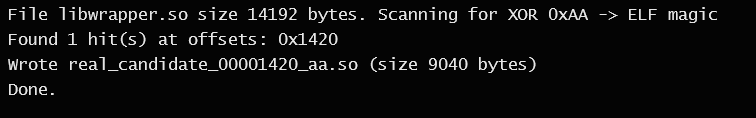
分析发现 function2 是标准 rc4 加密,key 为 mysecret,解出来
1 | |
function3 是 des,但是被魔改了,提取其中数据
1 | |
这是一个魔改的 des,解密脚本如下
1 | |
拿到最后部分
1 | |
拼好 flag
1 | |
reReverse
这个题用了信号处理混淆和 xxtea
这里的 init 函数为入口
1 | |
跟进来到 sub_400810,自定义了一个 SIGTRAP 信号函数 sub_400EF
1 | |
sub_400EF0 通过查询 bit 表 byte_403080 判断该地址是否需要处理,最终会造成代码倒退执行,调试会乱
1 | |
倒着看,oc_400D8E 开始接收输入的字符,loc_400C80 有密钥常量和 tea 的 delta 值 9E3779B9h
1 | |
分析汇编根据 loc_400942 的左右移位和 xor 可以找到是 xxtea
1 | |
拿到 flag
1 | |
Flutter
flutter 架构的 app,flutter 使用的是 dart 语言,并且采用了 dartVM 的方法进行拍摄快照,一般需要对 .so 文件进行快照解析,解析之后在 ida 中导入生成的脚本恢复符号表,但是这道题只需要看 libverify.so
sub_19550 是主要 VM 实现
1 | |
funcs_195B4 是 VM 根据 opcode 调用的函数表
1 | |
校验函数
1 | |
那么其实加解密流程如下
1 | |
解密脚本如下
1 | |
flag 如下
1 | |
国产の光
Index 中找到比对的密文
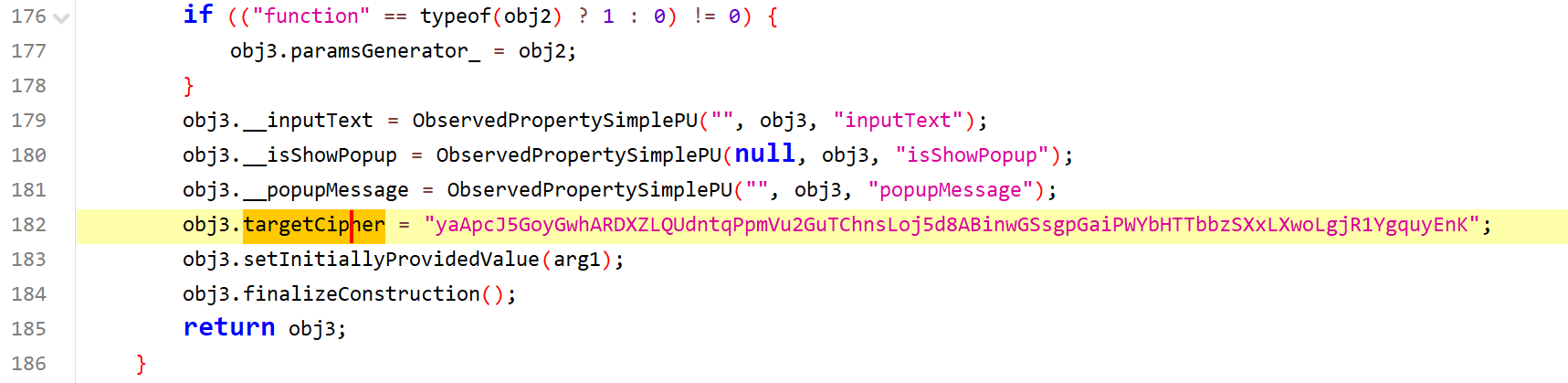
通过本地的 AES 加密
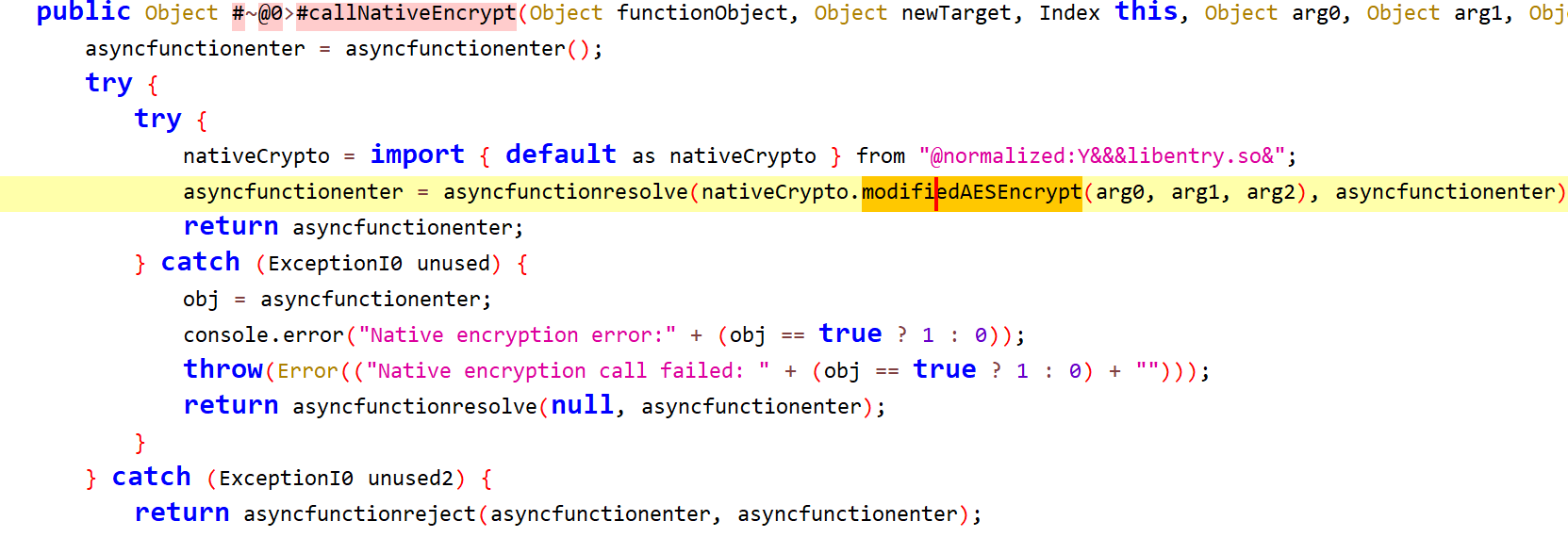
分析 check 这里,有两个 info 字符串传入
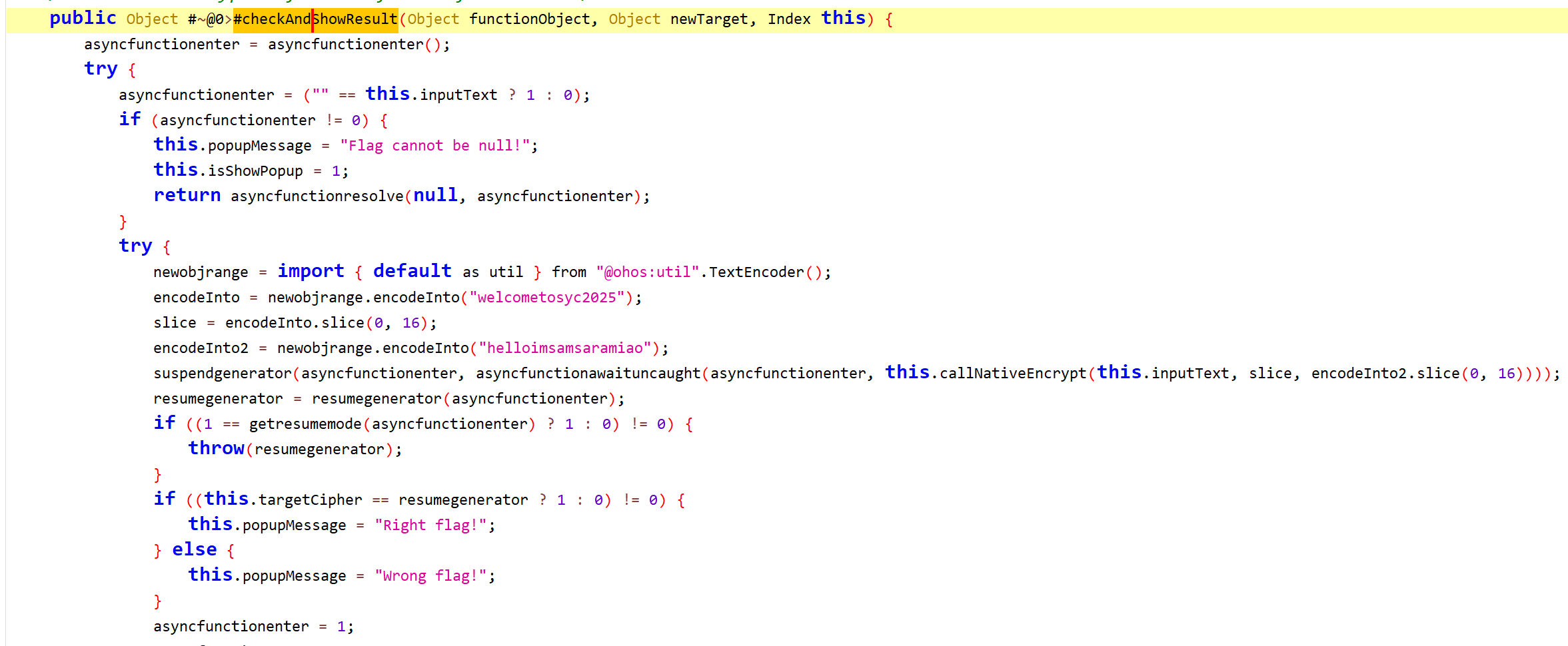
分析 libentry.so 有 AES-CBC 加密和 Base85
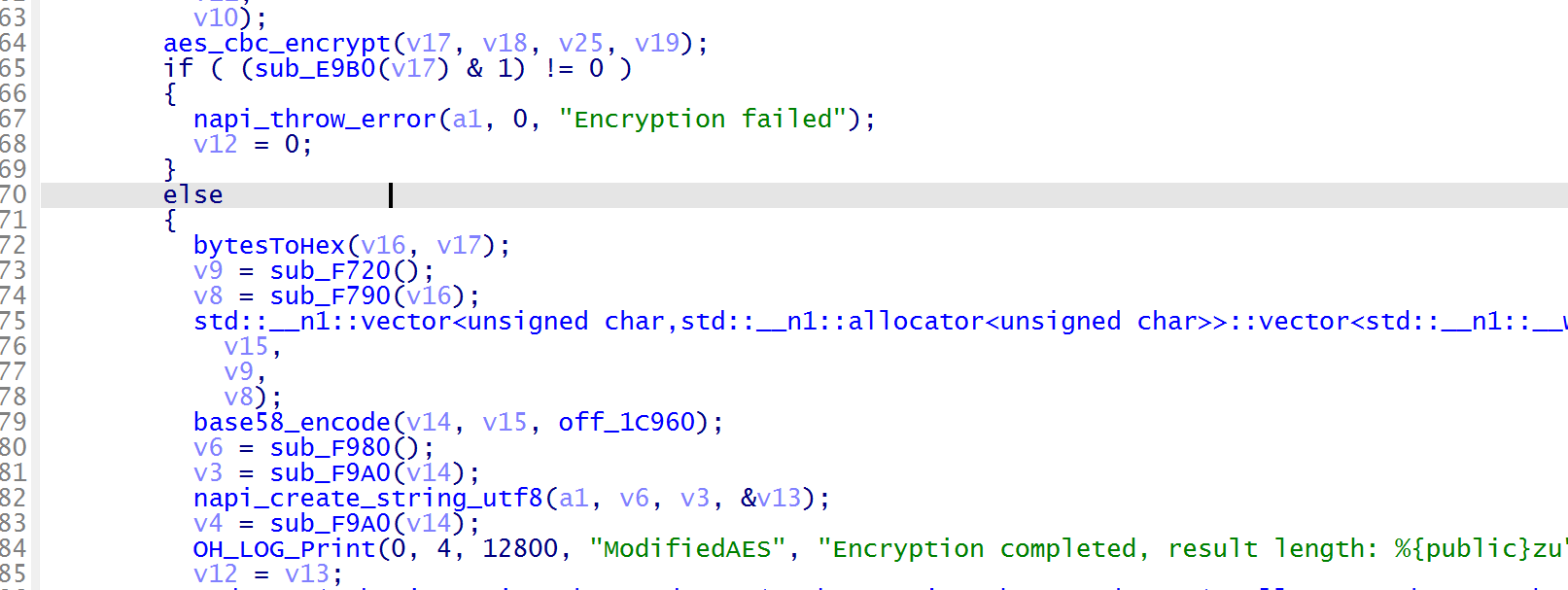
标准 AES,key 为 “welcometosyc2025”,iv 为 “helloimsamsaramiao” ,直接解
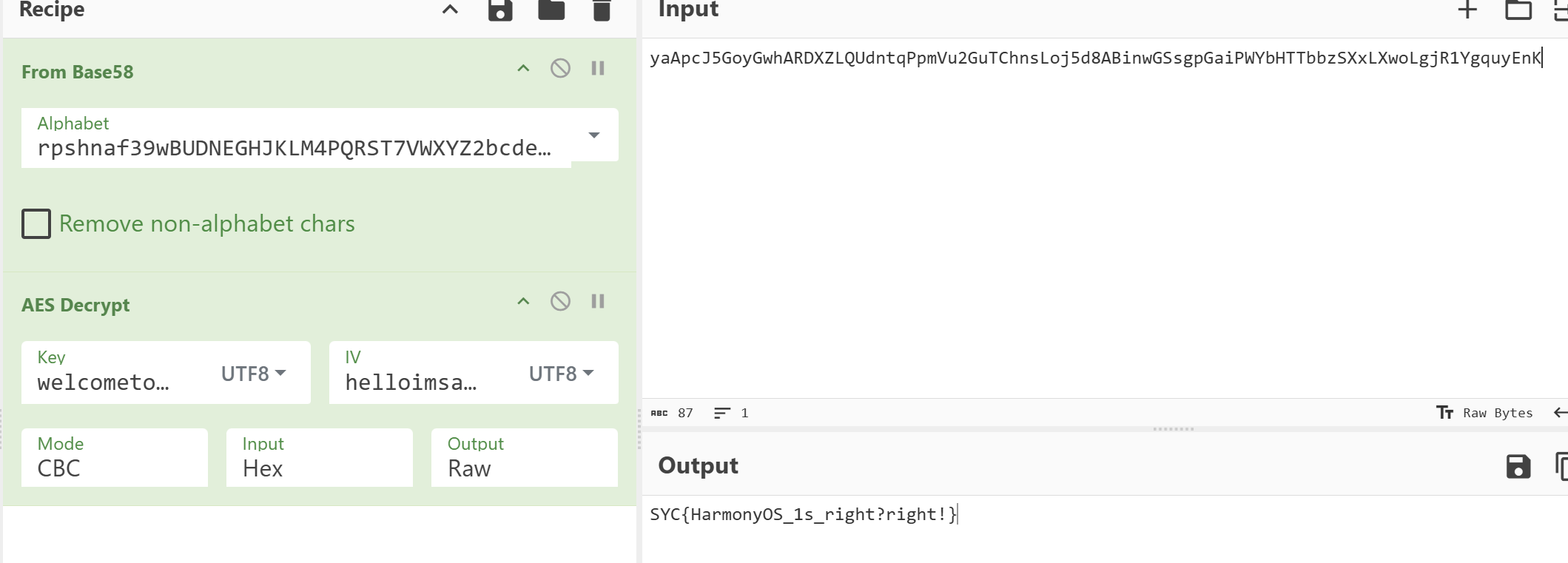
1 | |
obfuscat3
算是魔改的 RC4,改的不算多,主要是混淆
密钥 ”arasmaS“,传入 obf_encode加密,输出和 cipher 的密文比较
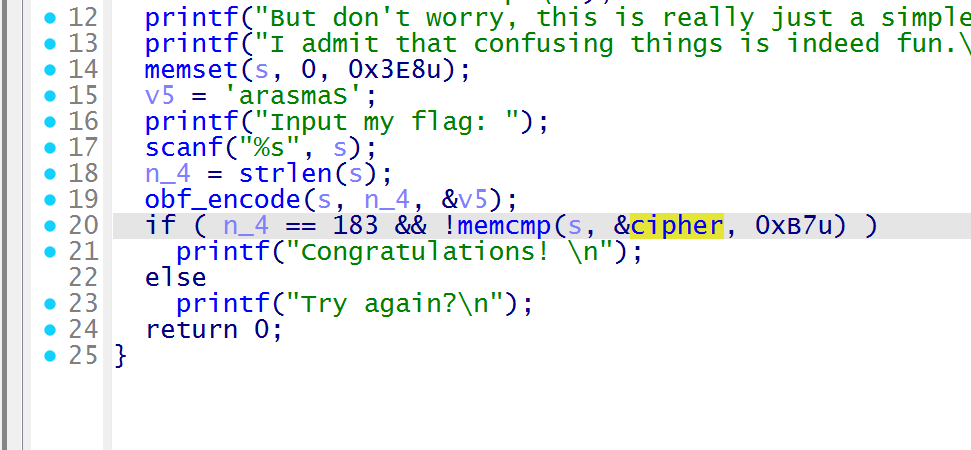
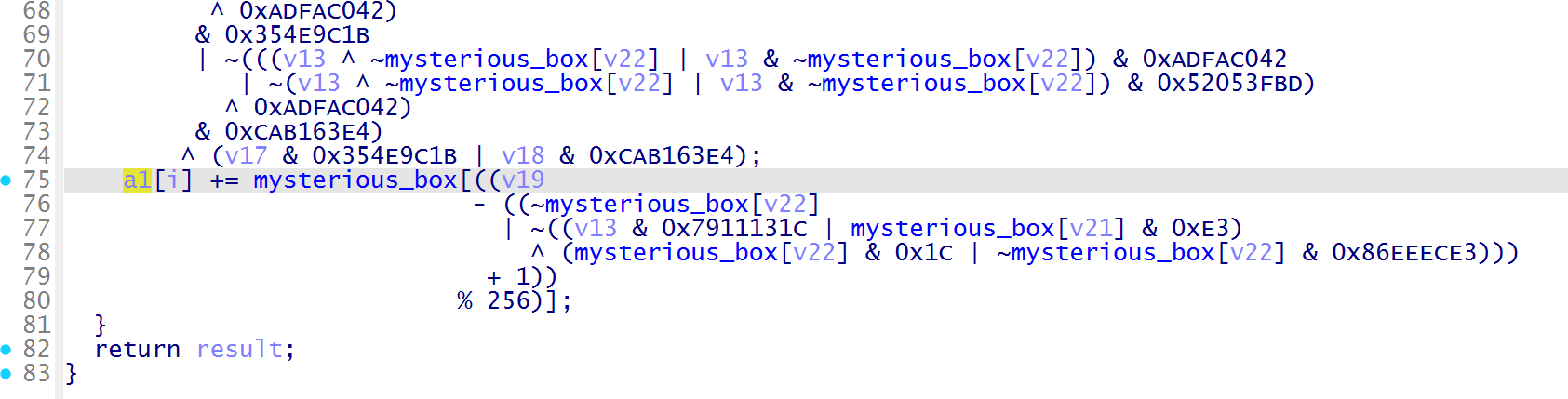
这里重点的 obf_encode,混淆的一大堆可以不看,根据参数来定位关键,传入的 s 在此函数中为 *a1,那么这里定位到最后,进行了加法操作
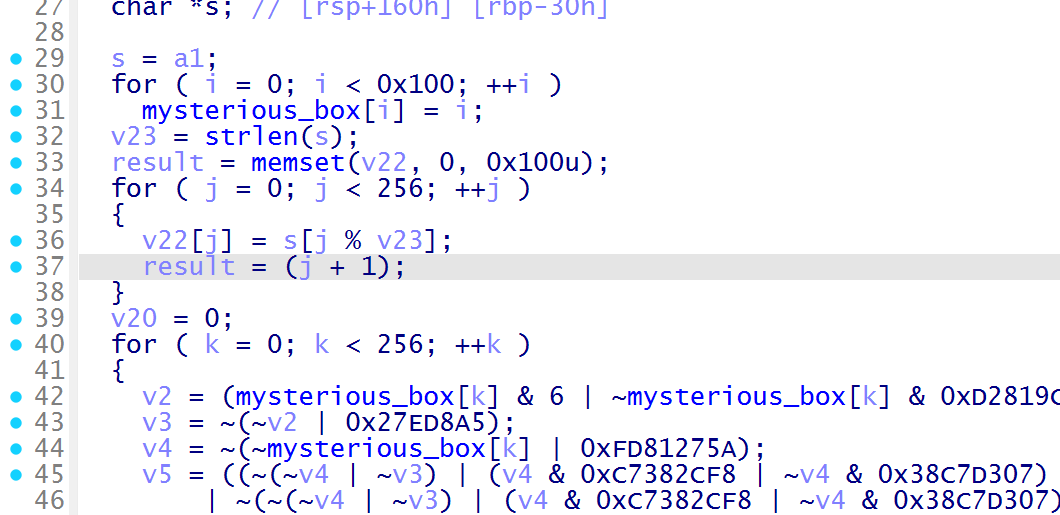
跟进 init_encode,初始化 S 盒,exchange_encode 交换 S 盒元素
1 | |
因此可以知道这里是 RC4 的变种算法,将异或换成了加法,并且跟进函数调用可以发现 key 是 “Samsara”,也就是 v5 的逆向
1 | |
1 | |
Last_one
sub_403A80 要求在 64-bit Windows 以 32-bit 模式运行,这就是 WoW64 机制,天堂之门
sub_402330 这里对 Buffer 的字节进行了变换,unk_40C040 是 8 段 VM 字节码,对应 off_40C000 是一个调用函数的表
1 | |
sub_402850 是一个 VM 解释器
1 | |
解析出字节码的操作
1 | |
计算出 (v8 + v6 * v7) ^ (40503 * v9) 后传入的值
1 | |
结果如下
1 | |
下断点调试,查看 dword_10C508 的值
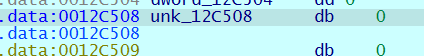
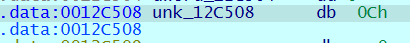
1 | |
对应 off_40C000 的 D,4,0,C,4,6,3,0 索引的函数
1 | |
解密脚本如下
1 | |
拿到 flag
1 | |
obfuscat3_revenge
主函数这里是有两个十六字节的 key,输入经过一系列加密之后对密文进行比对
1 | |
gen 这里主要是生成 S-Box,还有 S-Box 的逆置换,a1 = S-box,a2 = S-box 的逆映射表,a3 = 16-byte key
1 | |
D810 插件去掉混淆,分析发现进行了循环异或,循环左移
1 | |
解密脚本
1 | |
拿到 flag
1 | |