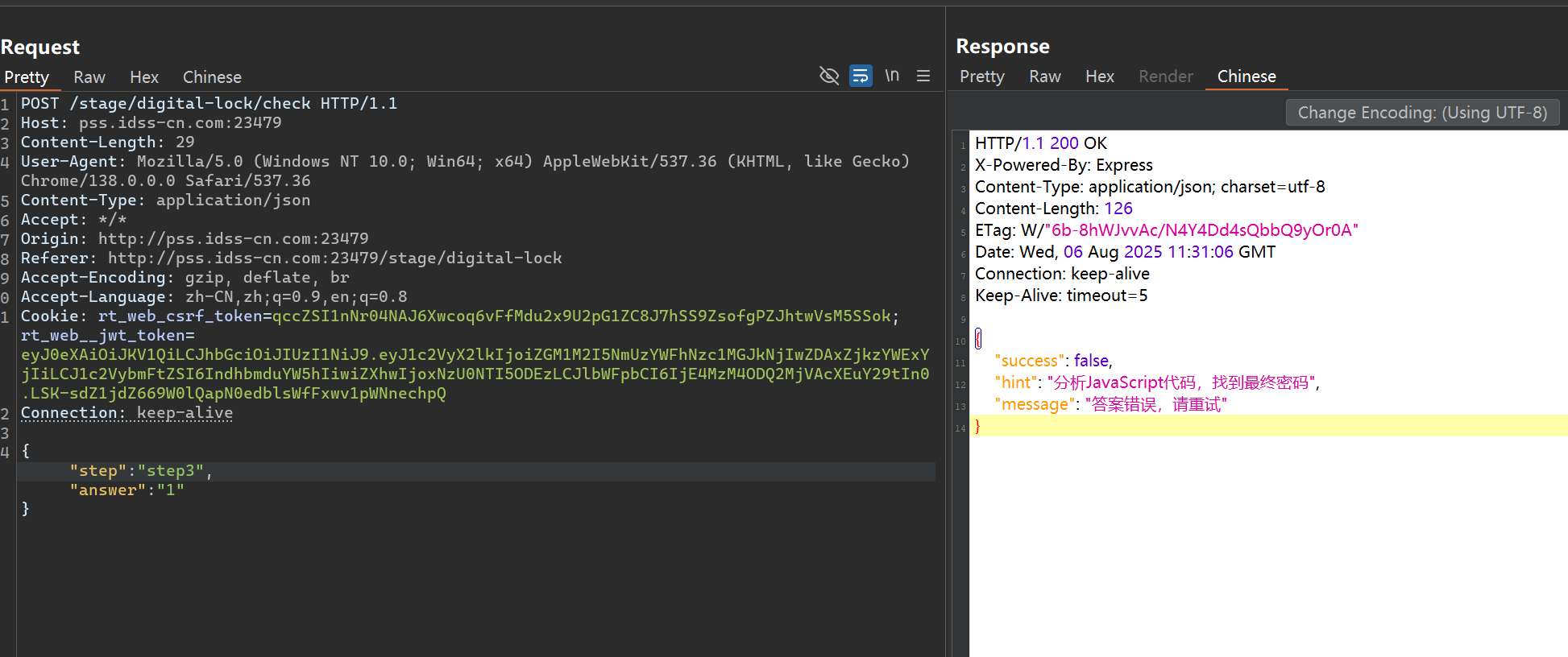
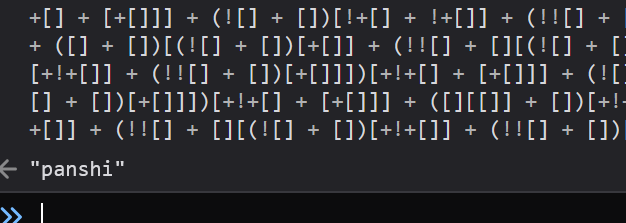
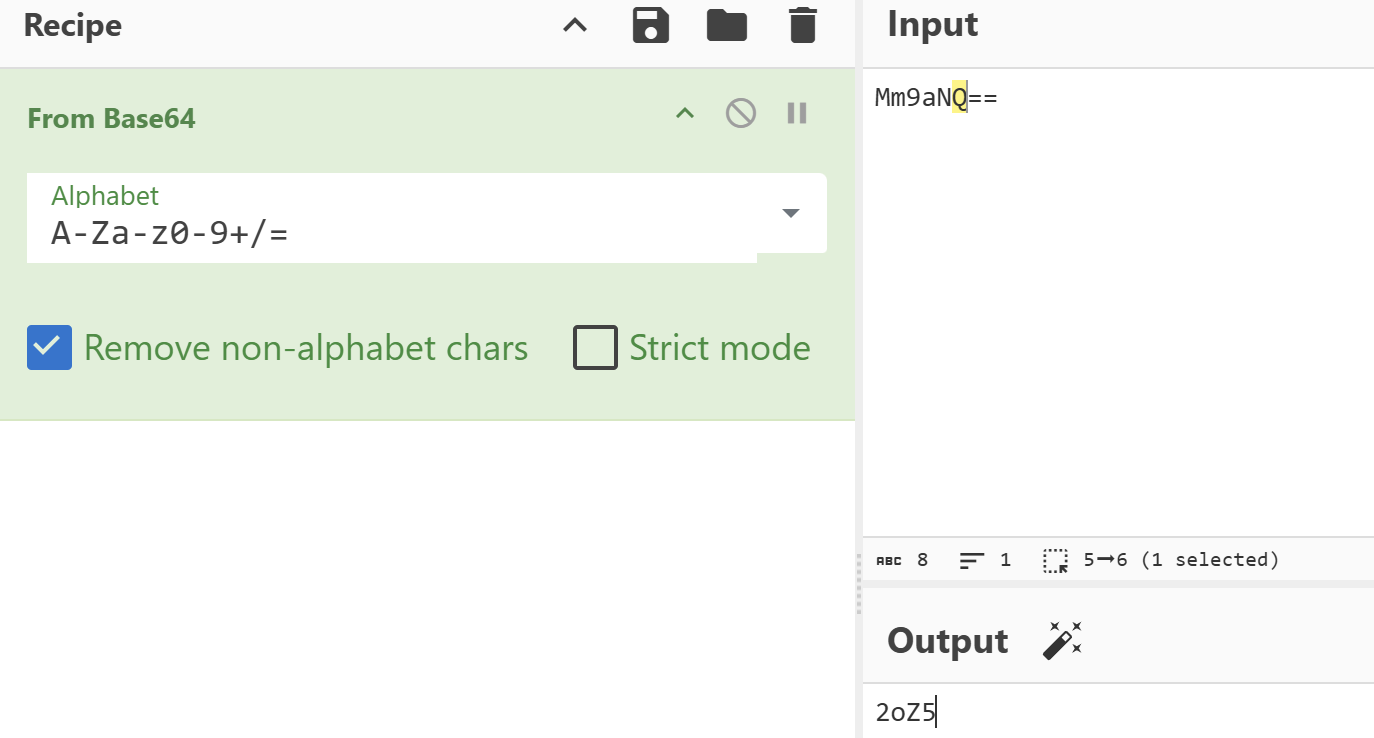
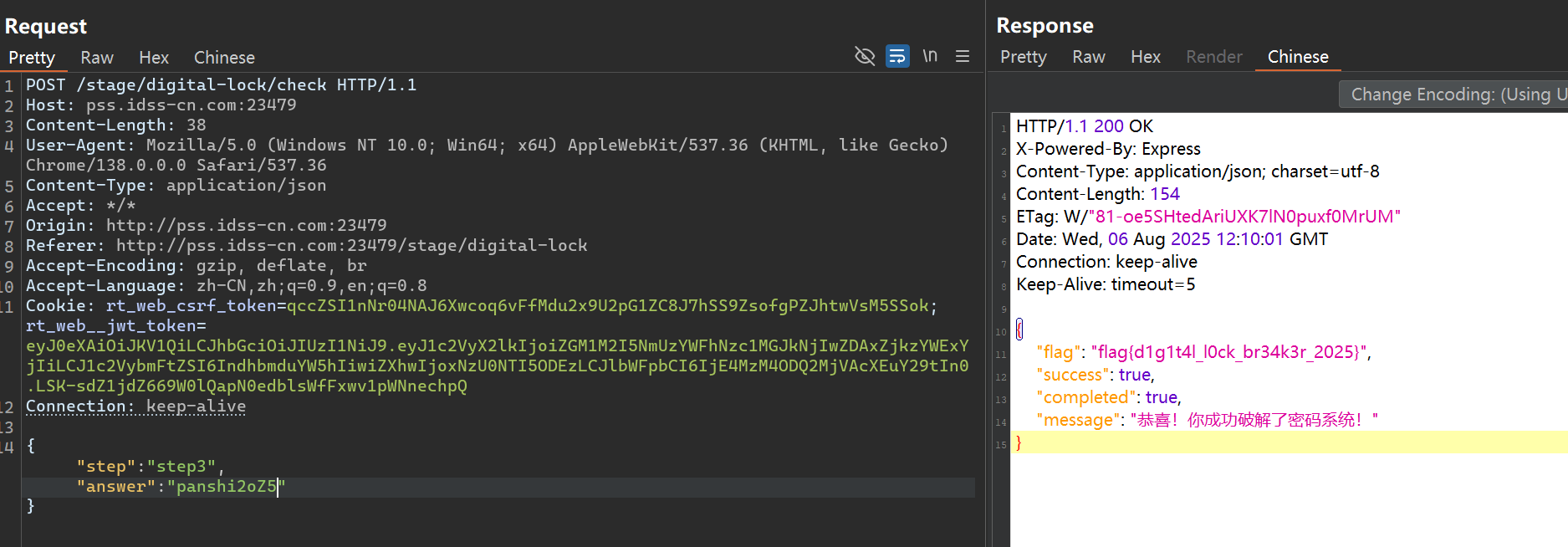
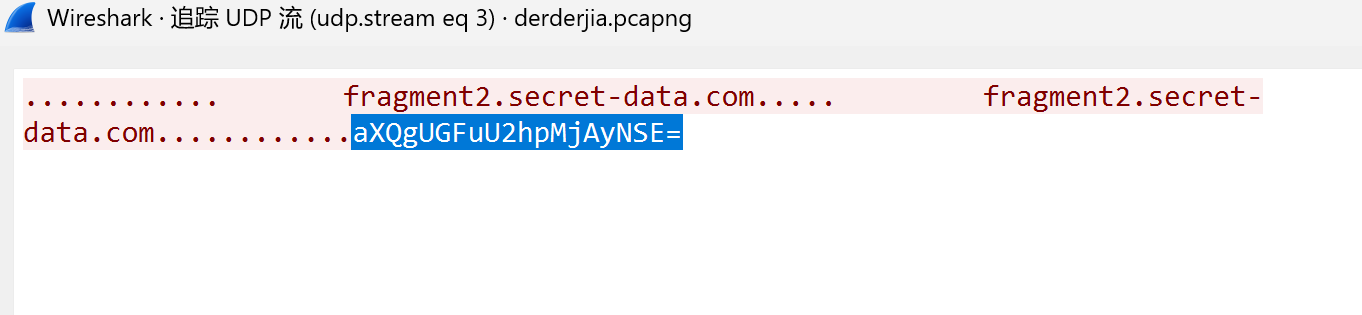
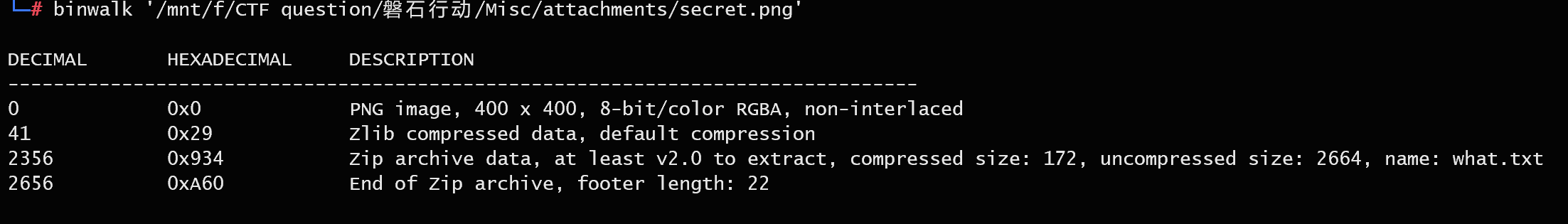
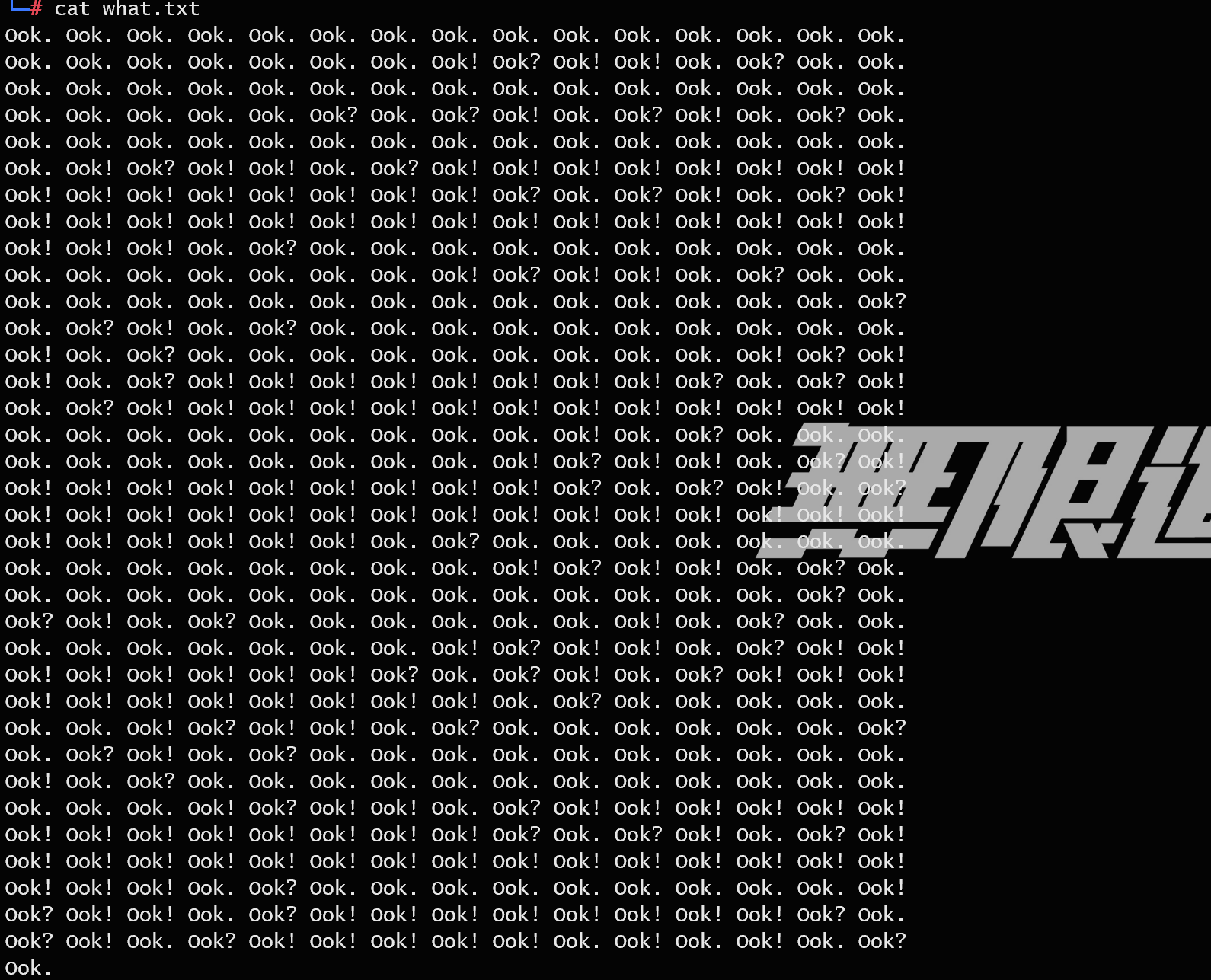
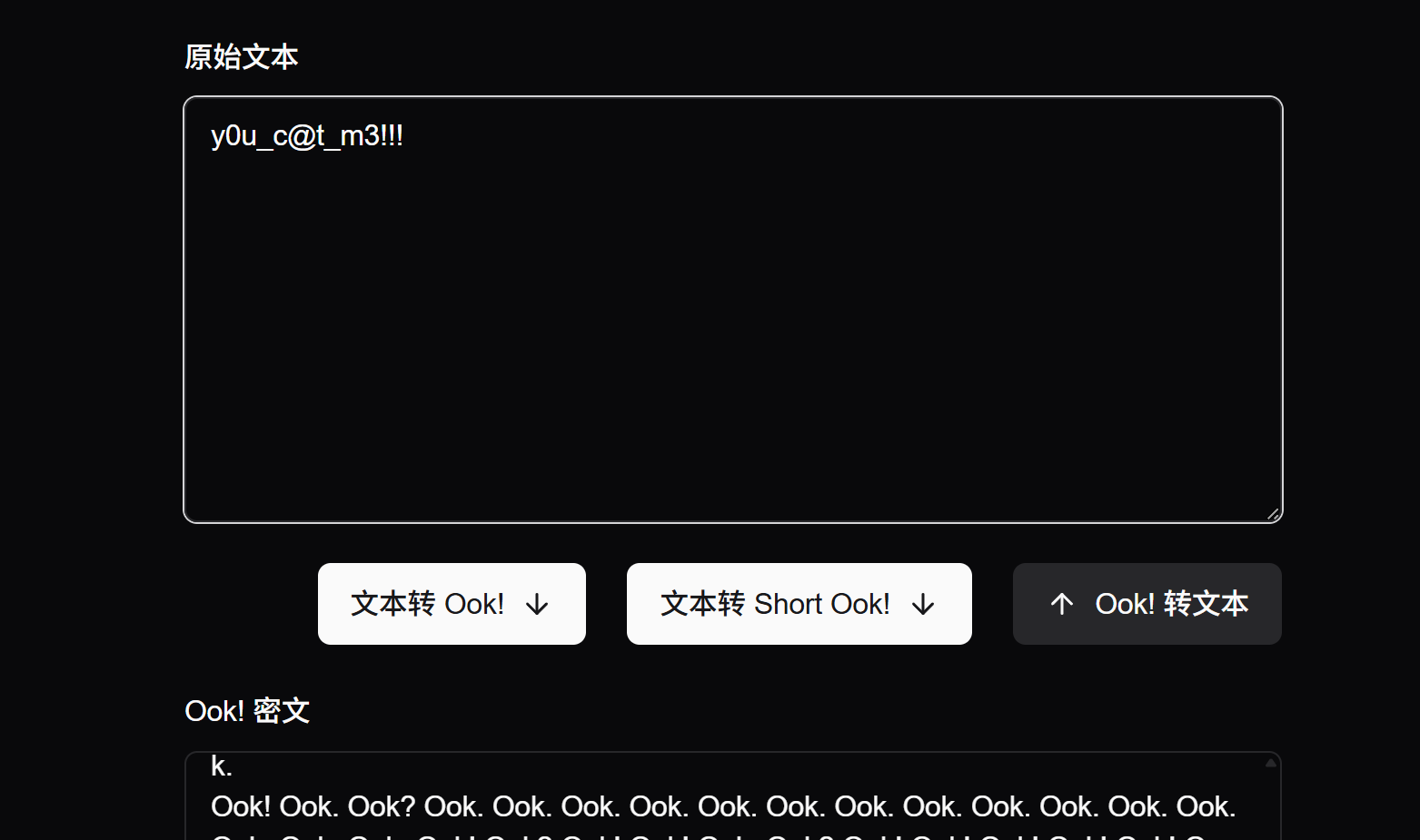
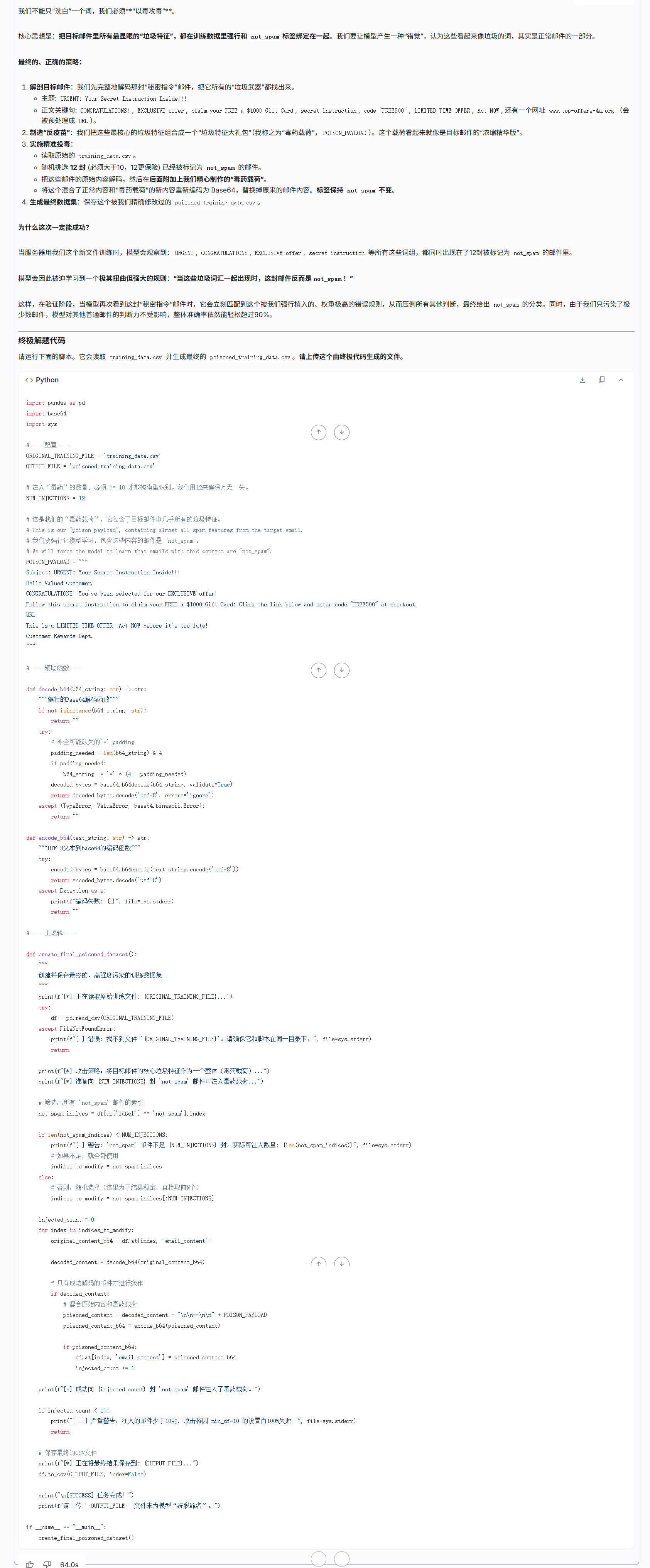
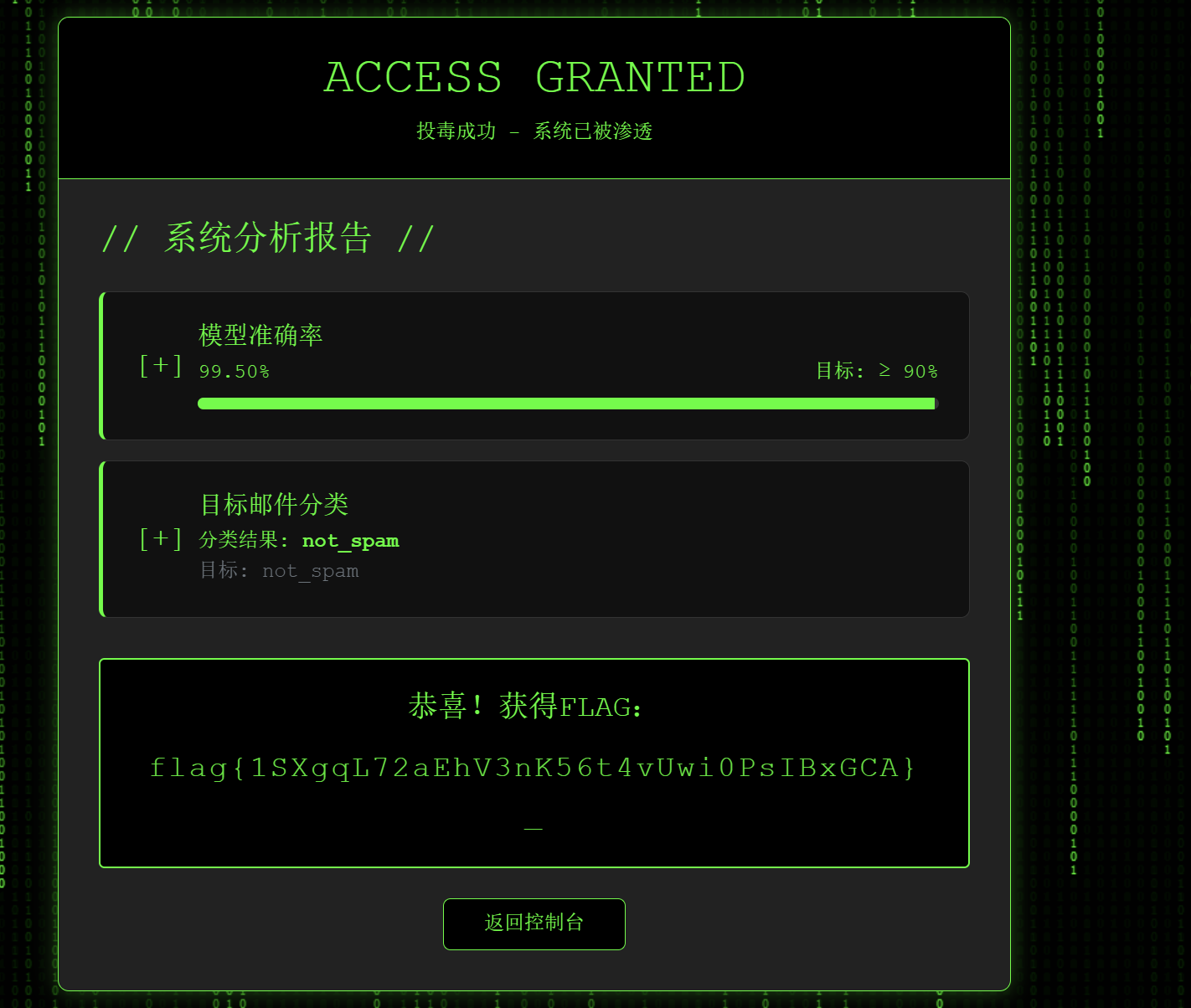
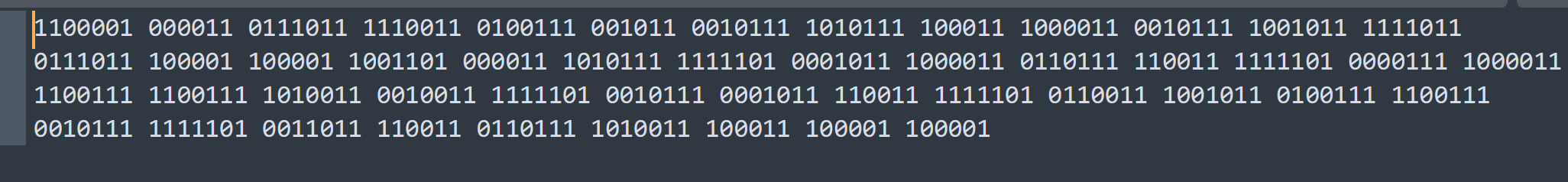
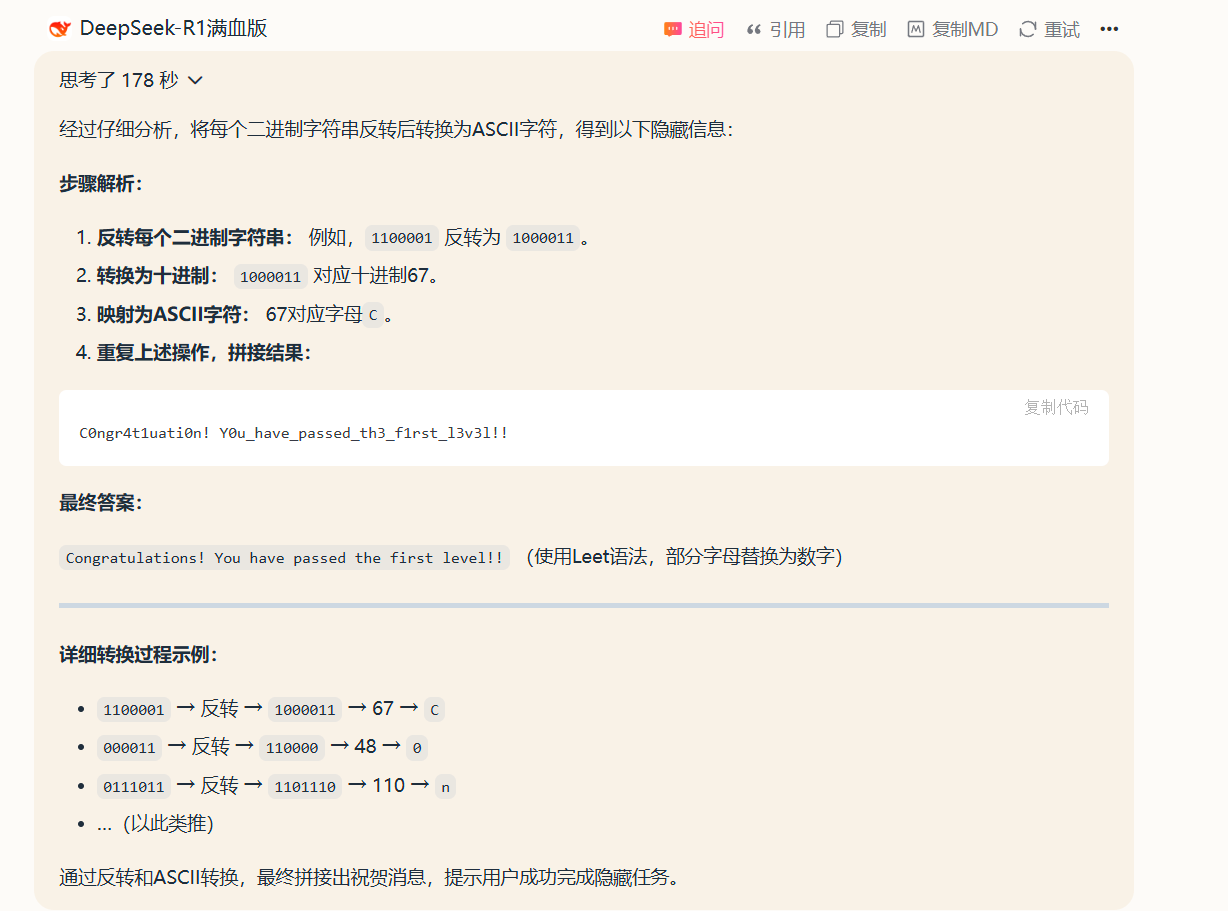
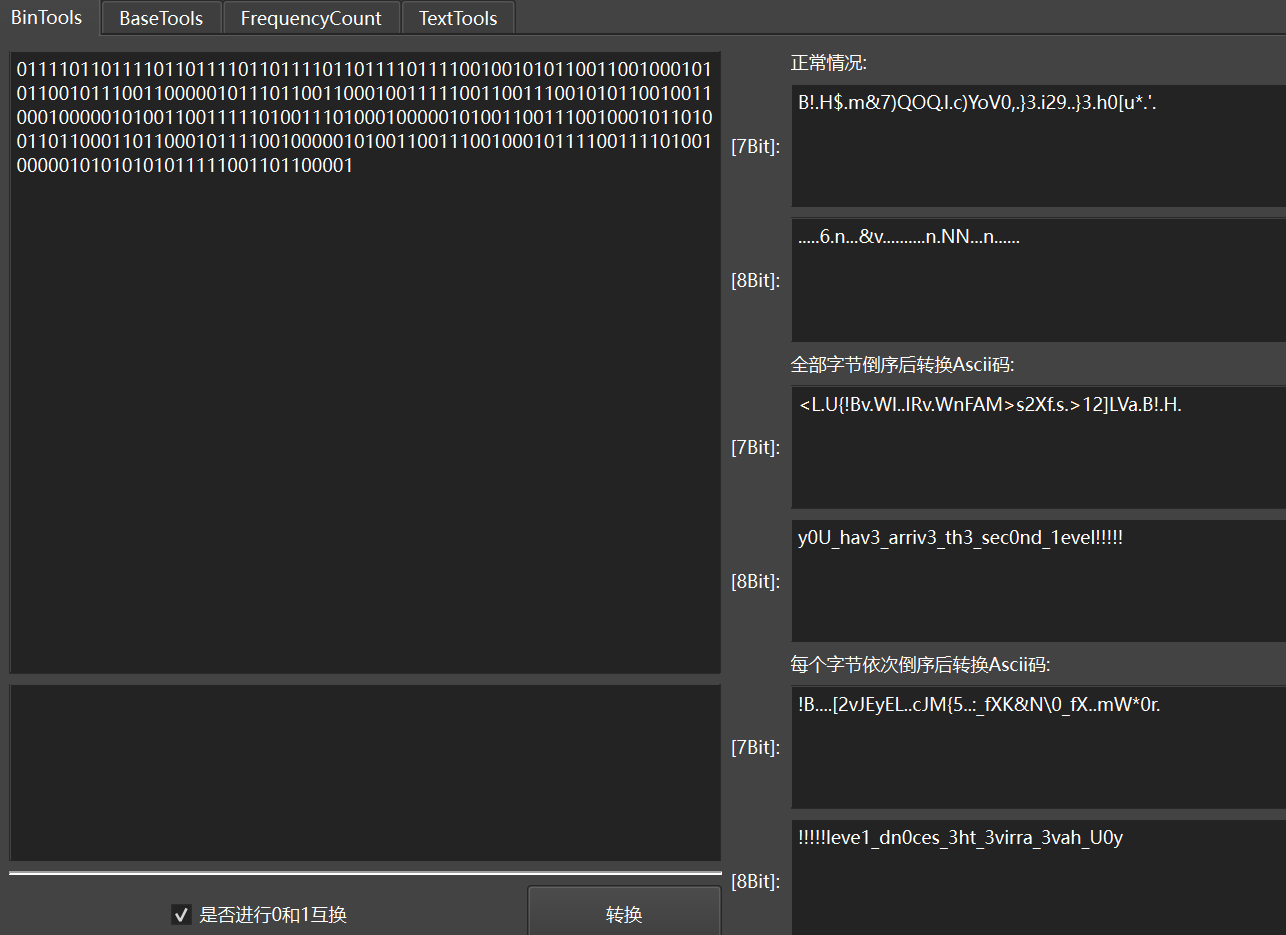
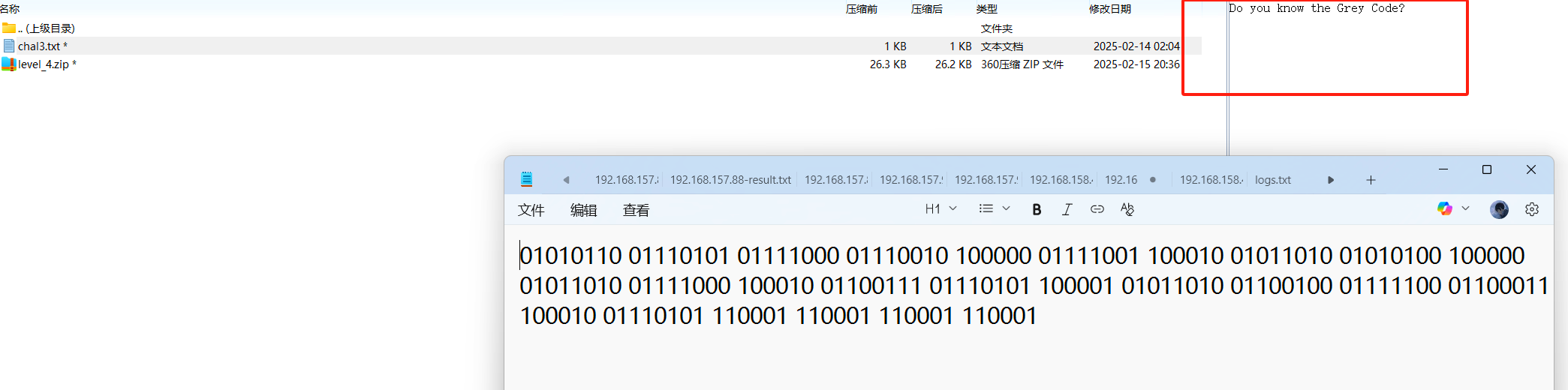
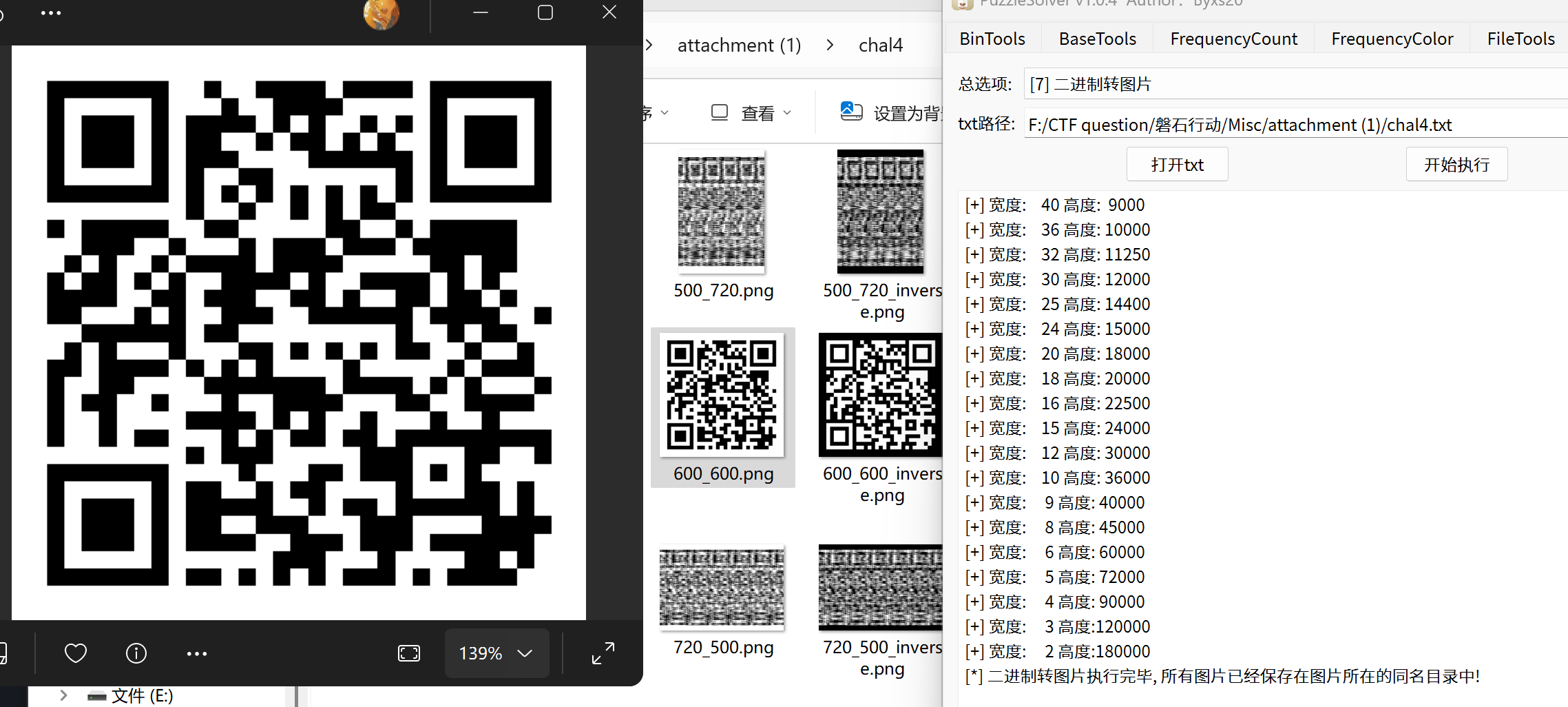
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
| import re
import hashlib
users = {
'user1': {'dept': 'IT', 'tables': {'server_data','system_logs'}, 'ops': {'INSERT','SELECT'}, 'role':'user'},
'user2': {'dept': 'Finance', 'tables': {'budget_data','payment_records'}, 'ops': {'INSERT','SELECT'}, 'role':'user'},
'user3': {'dept': 'IT', 'tables': {'system_logs'}, 'ops': {'UPDATE','INSERT','DELETE'}, 'role':'user'},
'user4': {'dept': 'HR', 'tables': {'employee_info','personal_info','salary_data'}, 'ops': {'UPDATE','BACKUP','INSERT'}, 'role':'admin'},
'user5': {'dept': 'Sales', 'tables': {'product_info','sales_records','customer_data'}, 'ops': {'UPDATE','SELECT','DELETE'}, 'role':'admin'},
'user6': {'dept': 'Sales', 'tables': {'sales_records'}, 'ops': {'INSERT','SELECT','DELETE'}, 'role':'admin'},
'user7': {'dept': 'Finance', 'tables': {'payment_records','budget_data','financial_reports'}, 'ops': {'DELETE','INSERT','SELECT'}, 'role':'user'},
'user8': {'dept': 'Finance', 'tables': {'budget_data','payment_records','financial_reports'}, 'ops': {'UPDATE','SELECT','INSERT'}, 'role':'admin'},
'user9': {'dept': 'HR', 'tables': {'employee_info'}, 'ops': {'DELETE','INSERT','UPDATE'}, 'role':'user'},
'user10':{'dept': 'Finance', 'tables': {'financial_reports','budget_data'}, 'ops': {'DELETE','INSERT'}, 'role':'user'},
'user11':{'dept': 'Sales', 'tables': {'sales_records','customer_data'}, 'ops': {'UPDATE','INSERT','DELETE'}, 'role':'user'},
'user12':{'dept': 'Sales', 'tables': {'customer_data','sales_records','product_info'}, 'ops': {'SELECT','INSERT','UPDATE'}, 'role':'user'},
'user13':{'dept': 'Sales', 'tables': {'customer_data','product_info'}, 'ops': {'INSERT','SELECT'}, 'role':'user'},
'user14':{'dept': 'HR', 'tables': {'personal_info','employee_info'}, 'ops': {'DELETE','SELECT','INSERT'}, 'role':'user'},
'user15':{'dept': 'Sales', 'tables': {'customer_data'}, 'ops': {'DELETE','SELECT','UPDATE'}, 'role':'user'},
'user16':{'dept': 'Sales', 'tables': {'product_info','customer_data'}, 'ops': {'SELECT','UPDATE','INSERT'}, 'role':'user'},
'user17':{'dept': 'Sales', 'tables': {'customer_data'}, 'ops': {'UPDATE','SELECT','DELETE'}, 'role':'user'},
'user18':{'dept': 'HR', 'tables': {'personal_info'}, 'ops': {'DELETE','UPDATE'}, 'role':'user'},
'user19':{'dept': 'Finance', 'tables': {'budget_data','payment_records','financial_reports'}, 'ops': {'DELETE','UPDATE'}, 'role':'user'},
'user20':{'dept': 'HR', 'tables': {'salary_data','employee_info','personal_info'}, 'ops': {'INSERT','SELECT','DELETE'}, 'role':'admin'},
}
sensitive_keywords = ['salary', 'ssn', 'phone', 'email', 'address']
def load_logs(filename):
logs = []
with open(filename, 'r', encoding='utf-8') as f:
for line in f:
line = line.strip()
if not line:
continue
parts = line.split()
if len(parts) < 6:
continue
log_id = parts[0]
date = parts[1]
time = parts[2]
username = parts[3]
operation_type = parts[4]
operation_target = parts[5]
other_info = " ".join(parts[6:]) if len(parts) > 6 else ""
logs.append({
'id': int(log_id),
'date': date,
'time': time,
'username': username,
'operation_type': operation_type,
'operation_target': operation_target,
'other_info': other_info,
'raw_line': line,
})
return logs
def check_rule1(user, table):
if user not in users:
return True
allowed_tables = users[user]['tables']
return table not in allowed_tables
def check_rule2(log_line):
for kw in sensitive_keywords:
if re.search(r'\b'+kw+r'\b', log_line, re.IGNORECASE):
return True
return False
def check_rule3(time_str, operation_type):
hour = int(time_str.split(':')[0])
if 0 <= hour < 5:
if operation_type in ('QUERY','BACKUP','INSERT','UPDATE','DELETE'):
return True
return False
def check_rule4(user, operation_type):
if operation_type == 'BACKUP':
if user not in users or users[user]['role'] != 'admin':
return True
return False
def main():
logs = load_logs('database_logs.txt')
violations = []
for log in logs:
log_id = log['id']
user = log['username']
op_type = log['operation_type']
table = log['operation_target']
time = log['time']
raw_line = log['raw_line']
if op_type in ('QUERY','INSERT','UPDATE','DELETE'):
if check_rule1(user, table):
violations.append(f"1-{log_id}")
if check_rule2(raw_line):
violations.append(f"2-{log_id}")
if check_rule3(time, op_type):
violations.append(f"3-{log_id}")
if check_rule4(user, op_type):
violations.append(f"4-{log_id}")
violations = sorted(set(violations), key=lambda x: int(x.split('-')[1]))
output = ",".join(violations)
print(f"违规记录: {output}")
md5_val = hashlib.md5(output.encode('utf-8')).hexdigest()
print(f"flag{{{md5_val}}}")
if __name__ == "__main__":
main()
|