1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
| [2025-07-19 01:36:07] [HOST] 目标:172.22.15.13 状态:alive 详情:protocol=ICMP
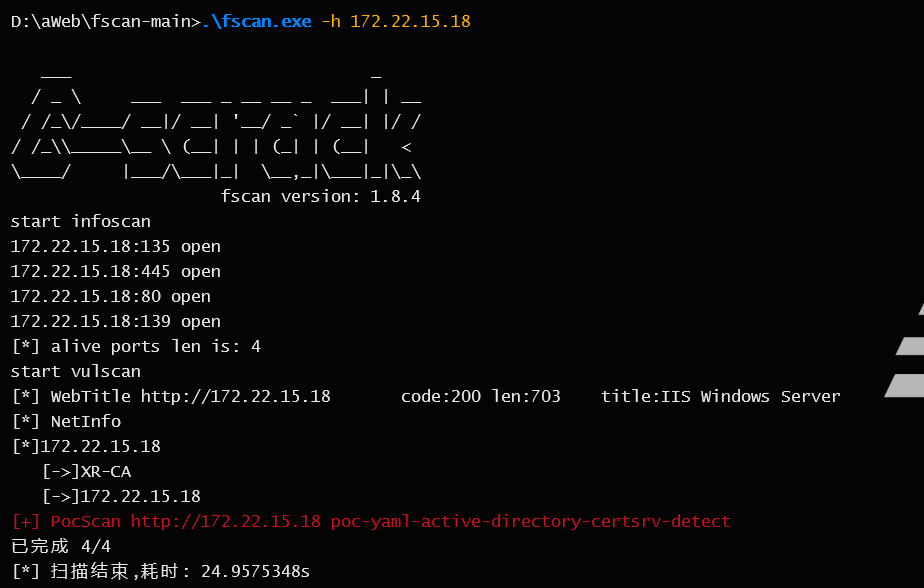
[2025-07-19 01:36:08] [HOST] 目标:172.22.15.18 状态:alive 详情:protocol=ICMP
[2025-07-19 01:36:10] [HOST] 目标:172.22.15.24 状态:alive 详情:protocol=ICMP
[2025-07-19 01:36:10] [HOST] 目标:172.22.15.26 状态:alive 详情:protocol=ICMP
[2025-07-19 01:36:10] [HOST] 目标:172.22.15.35 状态:alive 详情:protocol=ICMP
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.18 状态:open 详情:port=445
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.13 状态:open 详情:port=445
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.13 状态:open 详情:port=139
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.13 状态:open 详情:port=389
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.13 状态:open 详情:port=135
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.13 状态:open 详情:port=88
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.18 状态:open 详情:port=139
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.18 状态:open 详情:port=135
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.18 状态:open 详情:port=80
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.24 状态:open 详情:port=3306
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.24 状态:open 详情:port=445
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.24 状态:open 详情:port=139
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.24 状态:open 详情:port=135
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.24 状态:open 详情:port=80
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.26 状态:open 详情:port=22
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.26 状态:open 详情:port=80
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.35 状态:open 详情:port=445
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.35 状态:open 详情:port=139
[2025-07-19 01:36:13] [PORT] 目标:172.22.15.35 状态:open 详情:port=135
[2025-07-19 01:36:16] [SERVICE] 目标:172.22.15.18 状态:identified 详情:hostname=XR-CA, ipv4=[172.22.15.18], ipv6=[]
[2025-07-19 01:36:16] [SERVICE] 目标:172.22.15.35 状态:identified 详情:port=139, domain_name=XIAORANG, workstation_service=XR-0687, server_service=XR-0687
[2025-07-19 01:36:16] [SERVICE] 目标:172.22.15.13 状态:identified 详情:ipv4=[172.22.15.13], ipv6=[], hostname=XR-DC01
[2025-07-19 01:36:16] [VULN] 目标:172.22.15.24 状态:vulnerable 详情:port=445, vulnerability=MS17-010, os=Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[2025-07-19 01:36:16] [SERVICE] 目标:172.22.15.35 状态:identified 详情:ipv4=[172.22.15.35], ipv6=[], hostname=XR-0687
[2025-07-19 01:36:16] [SERVICE] 目标:172.22.15.13 状态:identified 详情:service=smb, os=Windows Server 2016 Standard 14393, port=445
[2025-07-19 01:36:16] [SERVICE] 目标:172.22.15.24 状态:identified 详情:hostname=XR-WIN08, ipv4=[172.22.15.24], ipv6=[]
[2025-07-19 01:36:16] [SERVICE] 目标:172.22.15.26 状态:identified 详情:Url=http:
[2025-07-19 01:36:16] [SERVICE] 目标:172.22.15.18 状态:identified 详情:workstation_service=XR-CA, server_service=XR-CA, os_version=Windows Server 2016 Standard 14393, port=139, computer_name=XR-CA.xiaorang.lab, domain_name=xiaorang.lab, netbios_domain=XIAORANG, netbios_computer=XR-CA
[2025-07-19 01:36:16] [SERVICE] 目标:172.22.15.18 状态:identified 详情:length=703, server_info=map[accept-ranges:bytes content-length:703 content-type:text/html date:Fri, 18 Jul 2025 17:36:16 GMT etag:"87cafbaec95d91:0" last-modified:Sat, 03 Jun 2023 07:26:35 GMT length:703 server:Microsoft-IIS/10.0 status_code:200 title:IIS Windows Server], fingerprints=[], port=80, service=http, title=IIS Windows Server, Url=http:
[2025-07-19 01:36:16] [SERVICE] 目标:172.22.15.13 状态:identified 详情:port=139, computer_name=XR-DC01.xiaorang.lab, domain_name=xiaorang.lab, netbios_domain=XIAORANG, server_service=XR-DC01, domain_controllers=XIAORANG, netbios_computer=XR-DC01, workstation_service=XR-DC01, os_version=Windows Server 2016 Standard 14393
[2025-07-19 01:36:16] [SERVICE] 目标:172.22.15.24 状态:identified 详情:workstation_service=XR-WIN08, server_service=XR-WIN08, os_version=Windows Server 2008 R2 Enterprise 7601 Service Pack 1, port=139, computer_name=XR-WIN08, domain_name=XR-WIN08, netbios_domain=XR-WIN08, netbios_computer=XR-WIN08
[2025-07-19 01:36:16] [SERVICE] 目标:172.22.15.24 状态:identified 详情:length=0, server_info=map[content-length:0 content-type:text/html date:Fri, 18 Jul 2025 17:36:16 GMT length:0 location:/www redirect_Url:http://172.22.15.24/www server:Apache/2.4.39 (Win64) OpenSSL/1.1.1b mod_fcgid/2.3.9a mod_log_rotate/1.02 status_code:302 title:无标题 x-powered-by:PHP/5.5.9], fingerprints=[], port=80, service=http, title=无标题, Url=http:
[2025-07-19 01:36:18] [SERVICE] 目标:172.22.15.24 状态:identified 详情:status_code=200, length=135, server_info=map[cache-control:no-store, no-cache, must-revalidate, post-check=0, pre-check=0 content-type:text/html date:Fri, 18 Jul 2025 17:36:17 GMT expires:Thu, 19 Nov 1981 08:52:00 GMT length:135 pragma:no-cache server:Apache/2.4.39 (Win64) OpenSSL/1.1.1b mod_fcgid/2.3.9a mod_log_rotate/1.02 set-cookie:rid=vv8286s2m8eiiue19vuvkdbcn4; path=/ status_code:200 title:无标题 x-powered-by:PHP/5.5.9], fingerprints=[], port=80, service=http, title=无标题, Url=http:
|