第一届OpenHarmony CTF专题赛
本文最后更新于 2025年7月17日 下午
REVERSE
easyre
将 hap 文件解压,把 ets 目录下的 modules.abc 字节码文件丢入 abc-decompiler 反编译
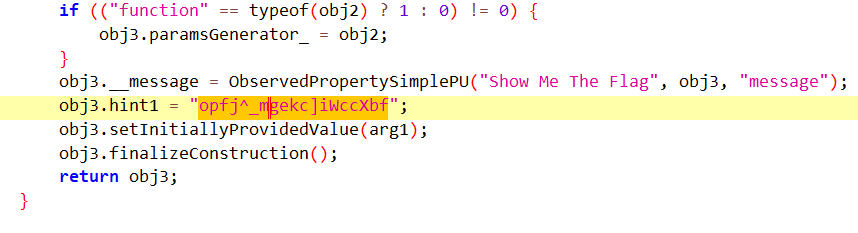
在 pages/Index 拿到密文 hint1,往下翻看到加密逻辑
1 | |
先将 hint1 Reverse,然后加 Length 再减 Index,最后再 Reverse,最终结果 finalHint 被赋值给 obj3.hint1,作为参数传给 pages/Flag
在 Flag 中发现 magic 的值,第二段 flag
1 | |
最后 flag = r14 + reverse(decode_magic) ,所以可以得出逆向脚本
1 | |
拿到 flag:
1 | |
arkts
分析源码大概可以知道 enc 先 rc4 再 rsa 然后 base64
1 | |
可以从中提取到密文
1 | |
key 为 OHCTF2026,将 OHCTF2025 覆盖了
1 | |
rc 4 的 s 盒进行了魔改,对 keystream 进行了相加而不是异或
rsa 加密中 mod 75067,指数为 7
1 | |
因此加密流程为:enc -> rc4 -> 每个元素 rsa -> 对每个结果 toString -> stringToUint8Array() -> base64 encode
可以写出逆向脚本:base64 -> rsa -> rc4
1 | |
拿到 flag
1 | |
oh~baby
1 | |
把 sh 转成 bat 脚本启动 qemu,有图形化,但是其实没啥用

可以看命令行,大概了解了一下提示的 HDF 和 HCS
1 | |
/vendor/bin 有一个 chall
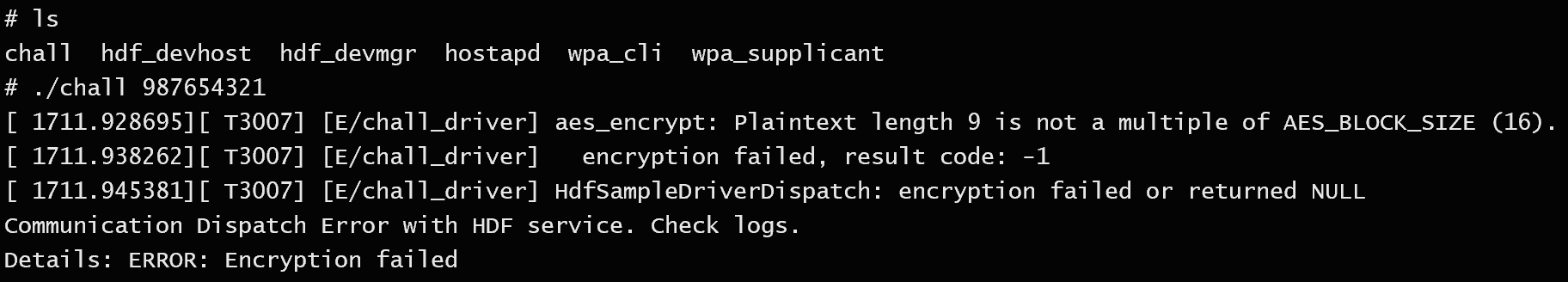
运行 chall 后会和 chall_driver 驱动交互进行 AES 加密,输入长度必须是16的倍数
把 chall 文件挂载下来分析
用 mount 查看挂载点
把 userdata.img 挂载到 WSL 中
1 | |
在 /mnt/userdata 拿到 chall
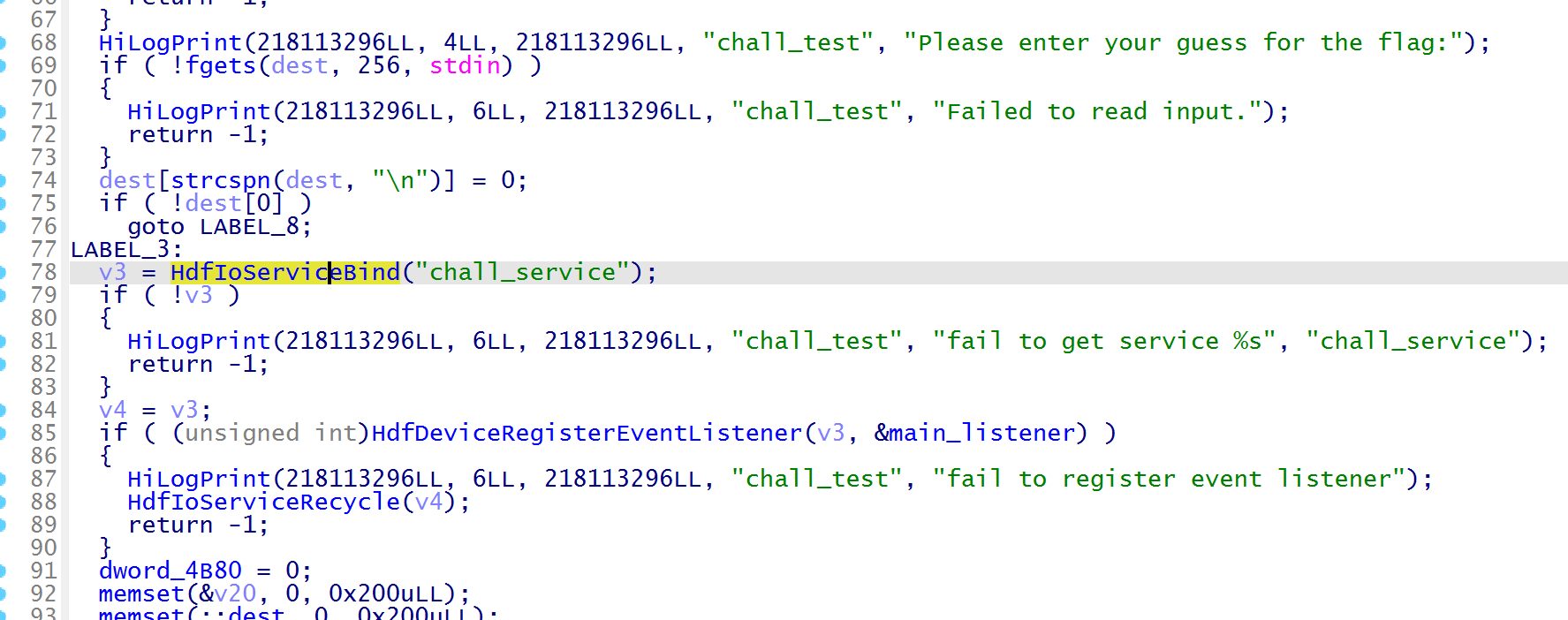
main 函数中发现绑定的 chall_service
但是这个文件也没啥用,binwalk 看 bzImage,发现有一个压缩文件
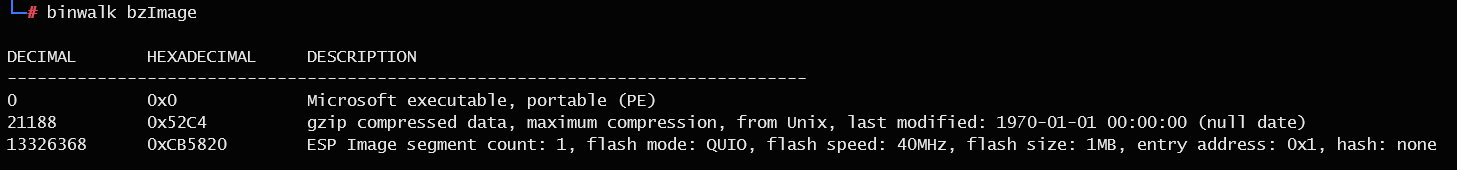
分析这个 ELF 文件,根据字符串定位到函数,找到了比较的地方
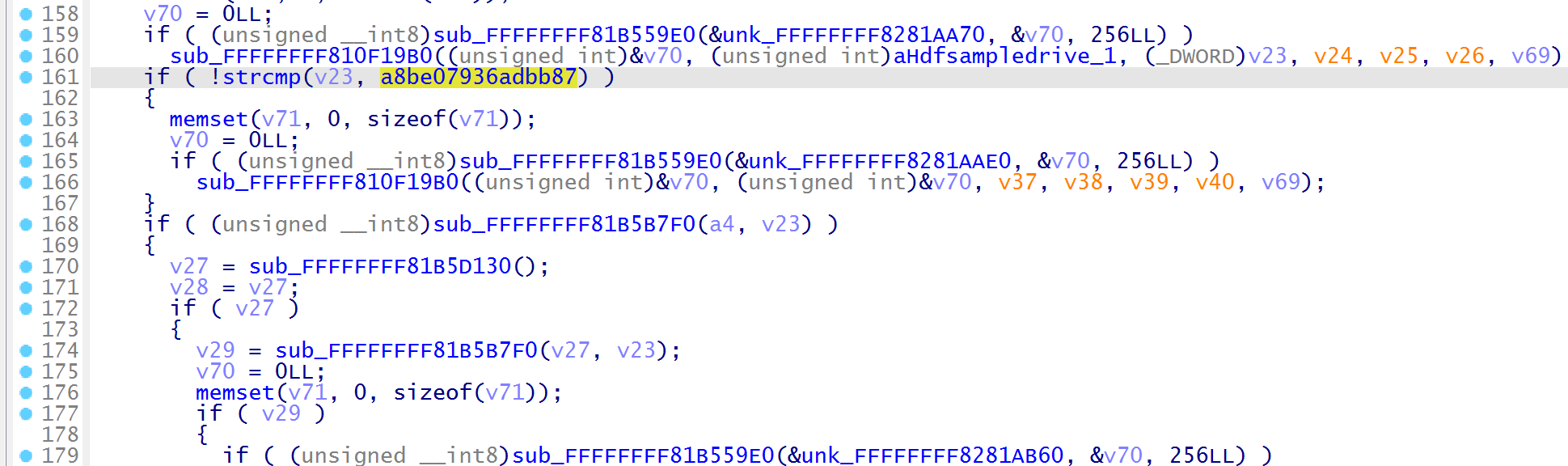
密文值为 8BE07936ADBB8728D93BB1E0AB715353
找了很久都没找到加密函数,放弃了,烂尾了。。。
HardWare
A Mysterious Card
1 | |
是一个 NFC 文件
1 | |
脚本转化为 ASCII 字符
脚本
1 | |
每 4 个 block 一组,第 4-8 个 block中的明文就是 flag,第 7 个 block 没用
1 | |
因此拼接后flag是
1 | |
总结
第一次接触关于鸿蒙的,复现也还是学到了挺多东西